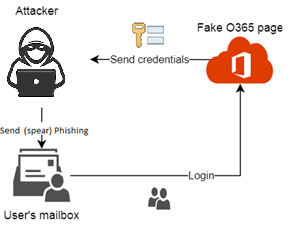
Many people tell you MFA is very important, and of course, they are right to tell you so… About 99.9% of compromised accounts aren’t equipped with MFA. Once logged in, the “attacker” gets full access to the mailbox, and they will start abusing the Mailbox.
For example, they could send more phishing emails to the user’s contacts. The attacker could also create a mailbox rule to either forward or simply delete all incoming mail.
Turning MFA on is not very difficult to do. All it requires is the Microsoft Authenticator app. After you’ve installed the app just go through the steps at: https://aka.ms/mfasetup
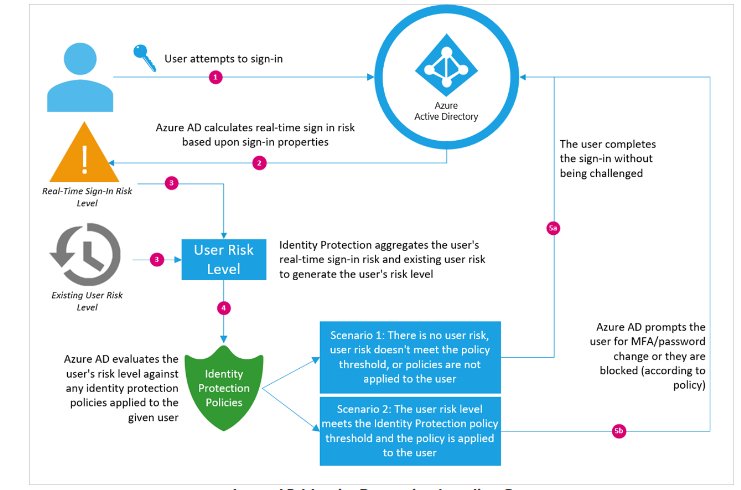
When MFA is active, security is 50% regulated, 50% you ask? Yes, 50%… Often the remaining 50% is forgotten. I’ll break the other 50% apart.
OAuth:
What is OAuth? OAuth is designed to allow a third-party application to access Microsoft services without disclosing user credentials. Users log in once and give an application permission to access certain functions (scopes).
OAuth can be abused to access the user’s mailbox with phishing by simply using a Phishing email asking for permission to run an App. You will see the beautiful Microsoft logo, surely it will be “familiar” and “safe”?
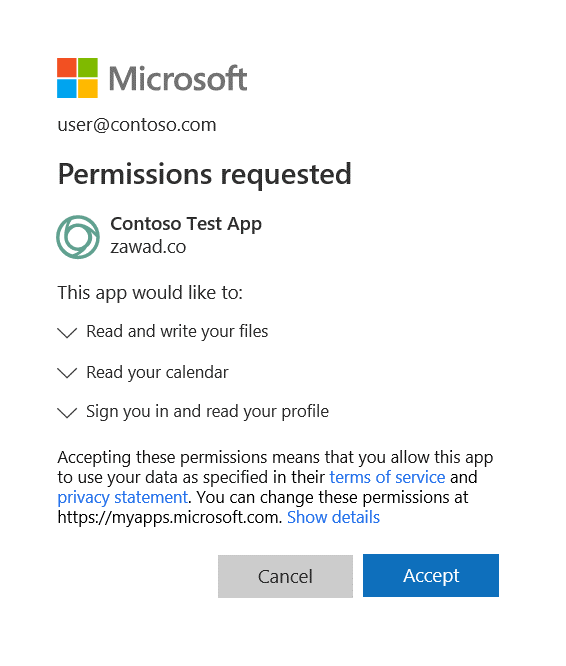
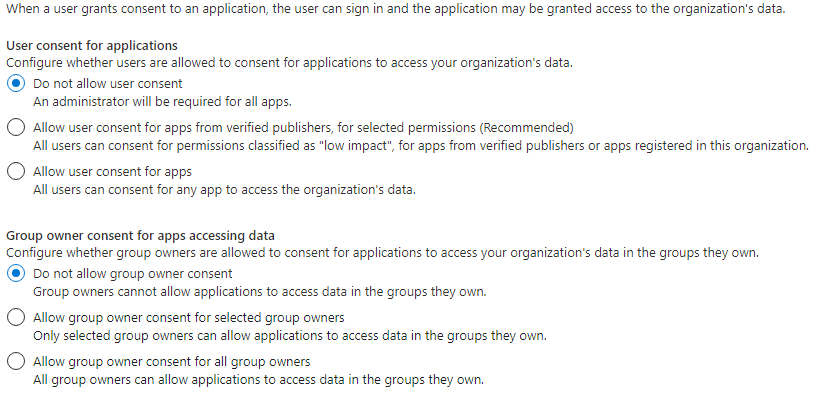
Not really…. When you blindly accept the conditions seen in the screenshot above, you could potentially give a malicious app access to your company data. All through a legitimate Microsoft security prompt. The only way to counter this effectively is to just switch the option: “Users can register applications” to NO.
You can find the settings in the Azure active directory –> user settings. If you want to define it a little more instead of just “No” or “yes”, open “Consent and Permissions” in the Enterprise Applications menu.
Legacy/Basic Authentication:
Enabling MFA does not affect the outdated authentication protocols: Pop3, Imap, Mapi, Activesync , and SMTP. Unfortunately, these protocols don’t support MFA.
My advice, take a look at Conditional access to block Legacy Authentication, or if you can just disable pop and IMAP protocols entirely with the following Powershell command:
Disable it for feature mailboxes:
Get-CASMailboxPlan -Filter {ImapEnabled -eq “true” -or PopEnabled -eq “true” } | set-CASMailboxPlan -ImapEnabled $false -PopEnabled $false
Disable it for existing mailboxes:
Get-CASMailbox -Filter {ImapEnabled -eq “true” -or PopEnabled -eq “true” } | Select-Object @{n = “Identity”; e = {$_.primarysmtpaddress}} | Set-CASMailbox -ImapEnabled $false -PopEnabled $false
Conditional Access:
What’s Conditional Access? This picture says it all:
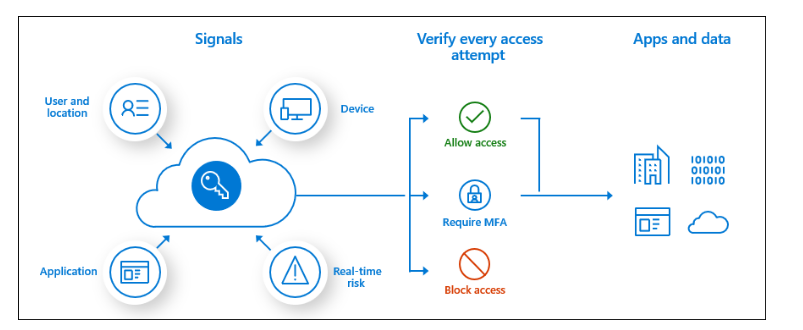
If this, than that.
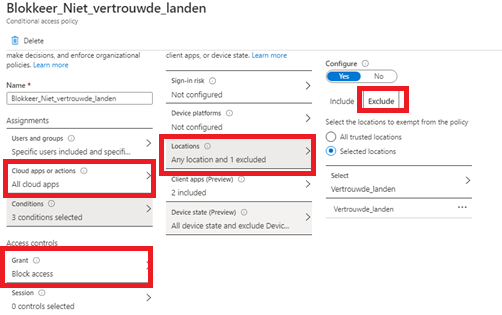
Conditional Access is a better way of blocking Legacy Authentication. But you can also do some other nice things with it. Like for example, block all non-approved countries to access your cloud apps (Sharepoint/Teams/Exchange Online, etc).
Office365 ATP:
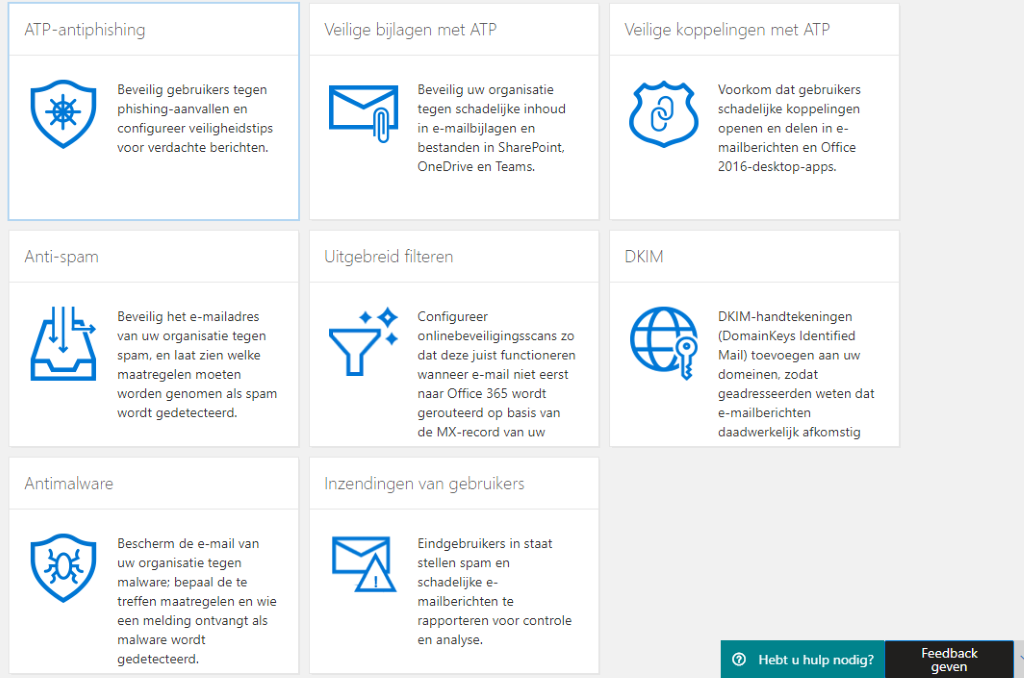
Office 365 ATP ensures that an anti-phishing policy is created within Office365. This policy ensures that phishing emails are blocked. Within Office 365 ATP, you can also configure safe links, safe attachments, and much more.
Users Awareness:
If MFA is enabled, users can register applications is turned off and legacy authentication is disabled, access to the company data is finally well protected. However, in the future, there will be new techniques to access company data through phishing. That makes user awareness a very important defense against phishing. There are many ways to train your users to recognize phishing emails; for example, you could do a fake phishing mail test to test and improve awareness among your users.
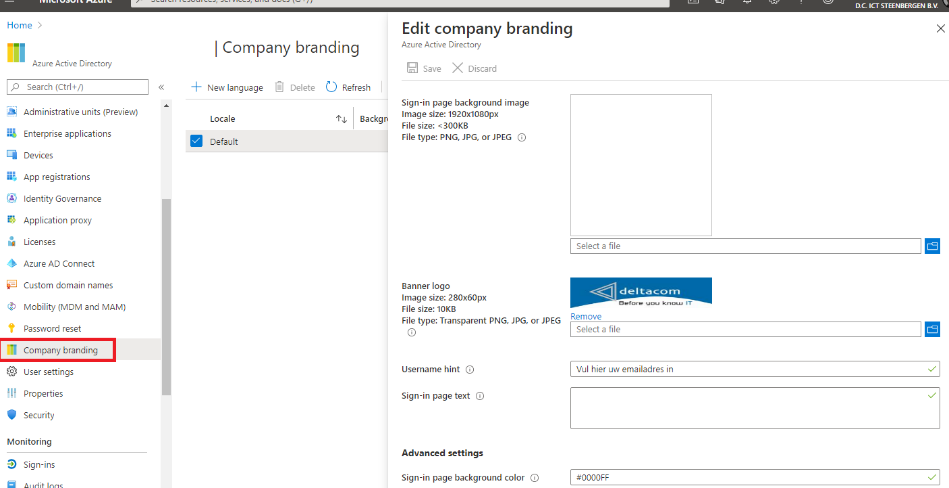
Customize Login pages:
This might seem like an unimportant step, but by ensuring your company logo is displayed on legitimate login pages, users might think twice when they see a login page not featuring their logo. This can be achieved by uploading your company logo in the company branding menu in the Azure active directory.
Conclusion:
When combining all these steps, you ensure that even if a user gives up his username and password, the attacker will be blocked by MFA. Disabling old protocols like IMAP and pop will ensure the attacker can’t bypass the MFA. Even when a user is prompted by a fake OAuth phishing mail, the user is not allowed to accept the request. Blocking countries from which a user won’t regularly log in further complicates the attacker’s attempt to access the user’s mailbox. As you can see, just MFA is not enough, but implementing the measures described in this article will cover the vulnerabilities still there after implementing MFA.
Further Recommendations:
*Passwords: Just make you have a good long password and you don’t have the same password set on ebay/paypal/etc and forgot to activate MFA on it .
*Identity Protection: If you have got money to spend, buy a license which includes azure ad p2.