This time, a simple blog about creating a Microsoft Edge Security baseline with the Settings Catalog (and administrative tools). I will also show you how to deploy and automate it with PowerShell!
I have created many blogs about securing your endpoints, data, and Microsoft 365, but I have not discussed making sure your Edge browser is configured and secured properly.
1.Background information
First, we will examine why you need to secure your Edge Browser. To secure Microsoft Edge, you can easily deploy the Microsoft Edge security Baseline in the Endpoint security Intune tab.
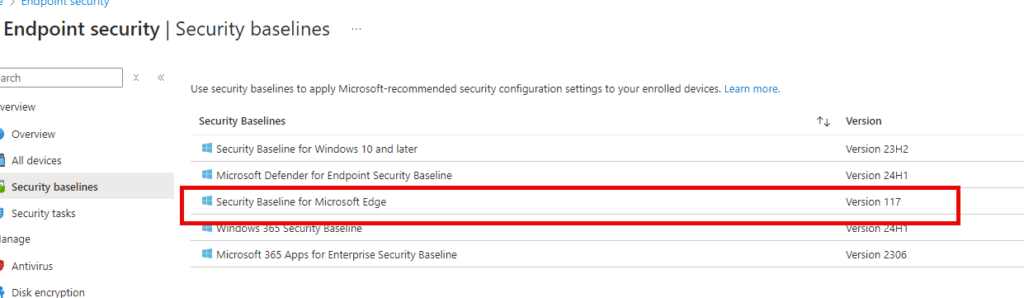
But I guess you might be asking yourself, why do I need to secure my Browser? Let’s examine some of the risks and mitigations.
Browser Extensions
Extensions, or add-ons, are simple tools that customize your browser experience and offer you more control. However, they could also redirect users to ads or phishing sites, collect user data, or download malware on infected systems.
The CacheFlow extension is one of the many examples
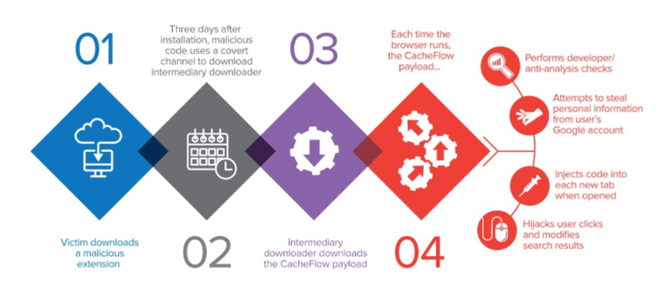
Extensions could also be downloaded from other sites, including sites that are infected with malware. It could install malicious extensions even without the users’ knowledge.
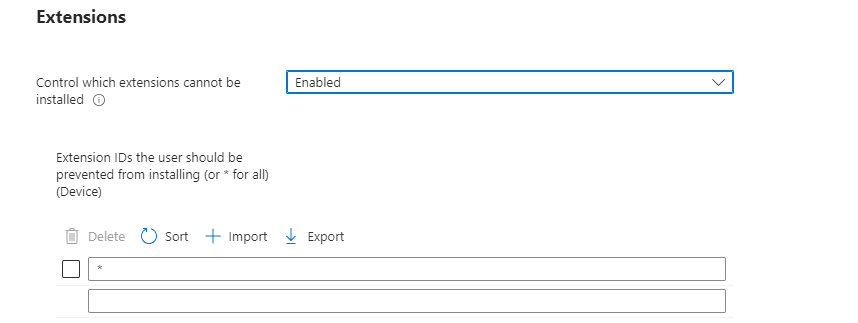
So, I guess blocking the possibility of adding extensions and specifying which extensions may and can be installed is the way to go.
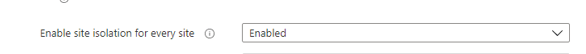
Site Isolation
Do you remember the Spectre attack from 2018? The Spectre vulnerability takes advantage of flaws in modern CPUs’ optimization features to circumvent the security mechanisms that prevent different processes from accessing each other’s memory space. Luckily, new CPUs have mitigated the Spectre vulnerability at the hardware level, but enabling site isolation mode is still important
With Site Isolation mode turned on, you could mitigate this attack. Site isolation is a security feature that separates web pages from each Site to its own process. Spectre attacks are all about inducing the processor to leak data at a specific moment. So let’s configure site isolation to make sure the hacker will find it more difficult to get their hands on some sensitive information.
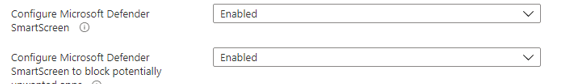
Defender SmartScreen
SmartScreen is a feature that helps protect your PC from downloaded malware and malicious websites. SmartScreen checks an application or file against a Microsoft database when downloading it. If Microsoft has the information that it is safe, SmartScreen will allow it to run. If Microsoft thinks it is dangerous malware, SmartScreen blocks it. It also ensures that malicious web content is blocked.

So this feature is very important to be configured and it has be enabled!
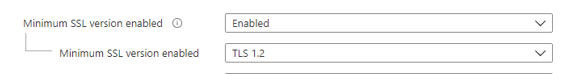
TLS
TLS is a cryptographic protocol that provides data encryption and authentication between different endpoints. It’s very important that these authentication and encryption are secured.
TLS versions:
TLS 1.0 was released in 1999. It has been known to be vulnerable to attacks like POODLE and BEAST.
TLS 1.1 has no known vulnerabilities, but it does not provide modern cipermodes.
TLS 1.2 keeps data being transferred across the network more secure.
TLS 1.3 has removed common vulnerabilities within the protocol strengthening overall security.
Luckily, Microsoft Edge version 84 disables the protocols TLS 1.0 and TLS 1.1 by default. However, it is still possible to react to these protocols, so we need to make sure TLS 1.2 is the minimum SSL version.
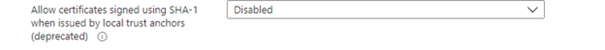
SHA-1
SHA-1 is most often used to verify that a file has been unaltered. This is done by producing a checksum before the file is transmitted and again once it reaches its destination.
However, in 2005, it was found insecure because SHA-1 has security weaknesses that make the hash particularly susceptible to collision attacks.
2.How you could automate the security and configuration of your Edge Browser with PowerShell
But this is only the hardening part. I guess you also need to define some other settings, like
- Enable the default search provider
- The default search provider url/name
- Configuring Smartscreen
- Automatically sign in with the work account
- Force synchronization
- Automatically import another browser’s data and settings at first run.
When you only want to deploy edge security settings, you could stick to the Security Baseline, but when you also want to deploy some additional settings, I recommend creating a new settings catalog or an administrative template.
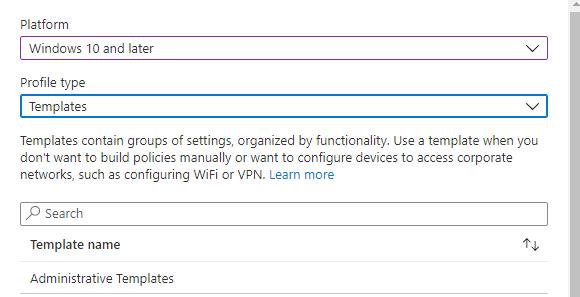
Deploying this for each tenant you enroll/configure can take a lot of your time, so you need to Automate it.
First, I will show you how to automate the deployment of administrative templates with PowerShell. If you are not interested in administrative templates but want to deploy them using the settings catalog, skip the first part.
1. Administrative Templates deployment with Powershell
So for now here is the zip File for the administrative templates. It contains the PowerShell script and the JSON files to deploy it to Intune.
https://call4cloud.nl/wp-content/uploads/2021/05/Edge-1.zip
I will look into the settings catalog as soon as possible!
2.Settings catalog deployment with PowerShell
First, here is some background information about retrieving the Settings Catalog. Let’s try to create a connection and retrieve the access token.
$clientId = "d1ddf0e4-d672-4dae-b554-9d5bdfd93547"
$redirectUri = "urn:ietf:wg:oauth:2.0:oob"
$resourceURI = "https://graph.microsoft.com/"
$authority = "https://login.microsoftonline.com/common"
$AadModule = Import-Module -Name AzureAD -ErrorAction Stop -PassThru
$adal = Join-Path $AadModule.ModuleBase "Microsoft.IdentityModel.Clients.ActiveDirectory.dll"
$adalforms = Join-Path $AadModule.ModuleBase "Microsoft.IdentityModel.Clients.ActiveDirectory.Platform.dll"
[System.Reflection.Assembly]::LoadFrom($adal) | Out-Null
[System.Reflection.Assembly]::LoadFrom($adalforms) | Out-Null
$authContext = New-Object "Microsoft.IdentityModel.Clients.ActiveDirectory.AuthenticationContext" -ArgumentList $authority
$platformParameters = New-Object "Microsoft.IdentityModel.Clients.ActiveDirectory.PlatformParameters" -ArgumentList "Always"
$authResult = $authContext.AcquireTokenAsync($resourceURI, $ClientID, $RedirectUri, $platformParameters)
$accessToken = $authResult.result.AccessToken
Now we established the connection we need to specify the URL where the configuration settings are stored
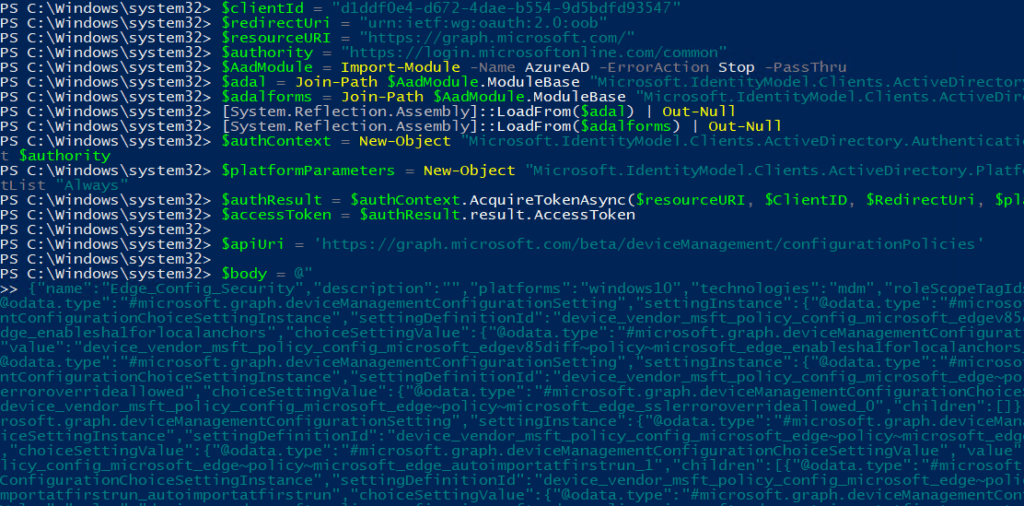
$apiUri = ‘https://graph.microsoft.com/beta/deviceManagement/configurationPolicies’
Let’s start invoking some stuff
$Data = Invoke-RestMethod -Headers @{Authorization = "Bearer $($authResult.result.AccessToken)"} -Uri $apiUri -Method get
$data.value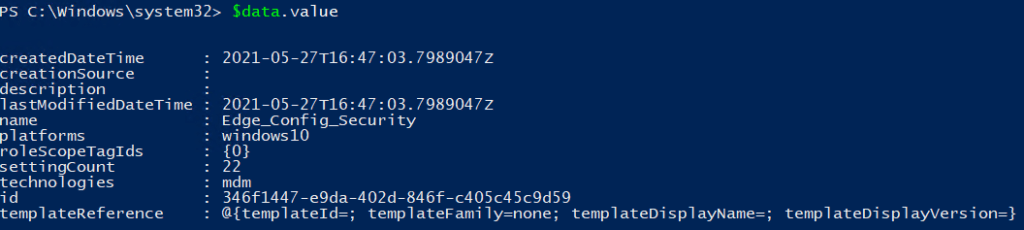
We need to take a note of the id, we will need it in the next step as we need to define the specific policy we want to take a good look at.
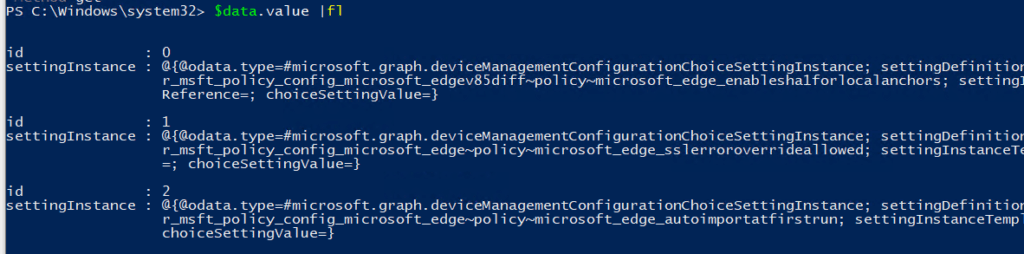
$apiUri = "https://graph.microsoft.com/beta/deviceManagement/configurationPolicies('ID')/settings"
$Data = Invoke-RestMethod -Headers @{Authorization = "Bearer $($authResult.result.AccessToken)"} -Uri $apiUri -Method get
$data.value | flAnd the results…
If you don’t want to use PowerShell to retrieve the settings, take a look at my blog about Fiddler.
https://call4cloud.nl/2020/11/close-encounters-of-fiddler
And now we are going to do the opposite, we are going to PUT something instead of GETting something
LINK TO THE EDGE SETTINGS CATALOG DEPLOYMENT POWERSHELL SCRIPT:
https://call4cloud.nl/wp-content/uploads/2021/05/deploy-edge.txt
Conclusion:
Don’t forget about securing your Edge Browser. Even when your devices are secure, your browser also needs to be secure. You really don’t want your browser to be responsible for a security breach.



This is so cool. Noob question, how do you generate the body in the PowerShell script? is there a funtional to generate this piece?
$body = @””
Hi,
Generating could be difficult. I Used the intune portal to create it and watch fiddler to get back the JSON/body I need