This blog will show you how you can wipe all devices even when you don’t have Intune (yet)
1. Introduction
The power of remote wiping your device is great to have. When your devices are enrolled in Intune and targetted with Autopilot, a remote wipe will make sure your devices will return to factory defaults and will begin to enroll your device back into Azure Ad and Intune.
The only thing you need to do is click on “Wipe” in Intune!
As told earlier, I have done a blog about this topic please read it, if you want to know exactly how all the reset/wipe options work:
https://call4cloud.nl/2021/04/to-retire-or-not-to-wipe
Transforming to a zero-trust modern workplace will require some work. You’ll need to set up Autopilot, collect the hardware hashes, remote wipe, and reset the device to let it enroll in Azure Ad with autopilot.
But how can you automate the process for remote wiping your domain devices without having your devices in Azure Ad or Intune and without the users being local admins? Especially in these times when devices exist everywhere! The only requirement for this solution is making sure your Windows 10 devices are domain joined and able to communicate with your domain controller.
2. The Local Device Option
Some time ago I wrote a blog about how to reset your device without Intune.
Of course, it’s a nice blog, but you need to be a local admin to perform this action. But when you have customers with an existing domain network and you have your trusty domain controller at your side, that’s no problem at all!
3. The Remote Option
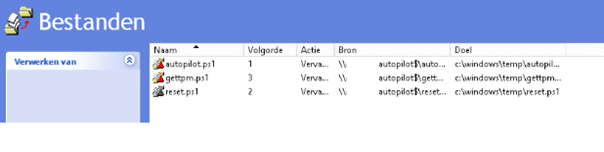
To begin your modern workplace journey and start collecting the device Hashes and resetting the device remotely, we need 2 PowerShell Scripts. The first one will collect your autopilot hashes. Alternatively, you could do it like this:
But with the solution above, the devices need to be accessible from the domain controller at the time when running the script.
Step 1: AutoPilot
This script will collect the hardware hashes needed for Autopilot and will save them on a file share. To be sure I have the hashes I am saving the hashes again. You can’t be to be careful
New-Item -Path c:\programdata\customscripts -ItemType Directory -Force -Confirm:$false | out-null
install-packageprovider -name nuget -minimumversion 2.8.5.201 -force | out-null
Save-Script -Name Get-WindowsAutoPilotInfo -Path c:\ProgramData\CustomScripts -force | out-null
$PCName = $env:COMPUTERNAME
c:\ProgramData\CustomScripts\Get-WindowsAutoPilotInfo.ps1 -OutputFile \\servername\autopilot$\csv\$pcname.csv
Step 2: Remote Wipe
The second part of the script will remote wipe your devices, please be very careful using it!!!!
set-executionpolicy -scope currentuser unrestricted -force
$ErrorActionPreference= 'silentlycontinue'
$global:ProgressPreference = 'SilentlyContinue'
$tenantname = “tenantname.onmicrosoft.com”
New-Item -Path c:\programdata\customscripts -ItemType Directory -Force -Confirm:$false | out-null
$reset =
@’
$namespaceName = "root\cimv2\mdm\dmmap"
$className = "MDM_RemoteWipe"
$methodName = "doWipeMethod"
$session = New-CimSession
$params = New-Object Microsoft.Management.Infrastructure.CimMethodParametersCollection
$param = [Microsoft.Management.Infrastructure.CimMethodParameter]::Create("param", "", "String", "In")
$params.Add($param)
try
{
$instance = Get-CimInstance -Namespace $namespaceName -ClassName $className -Filter "ParentID='./Vendor/MSFT' and InstanceID='RemoteWipe'"
$session.InvokeMethod($namespaceName, $instance, $methodName, $params)
}
catch [Exception]
{
write-host $_ | out-string
}
‘@
$start =
@’
reg.exe ADD HKCU\Software\Sysinternals /v EulaAccepted /t REG_DWORD /d 1 /f | out-null
Start-Process -FilePath "c:\ProgramData\CustomScripts\pstools\psexec.exe" -windowstyle hidden -ArgumentList '-i -s cmd /c "powershell.exe -ExecutionPolicy Bypass -file c:\programdata\customscripts\reset.ps1"'
‘@
#To made sure we have the autopilot hash before remote wipe
Save-Script -Name Get-WindowsAutoPilotInfo -Path c:\ProgramData\CustomScripts -force | out-null
$PCName = $env:COMPUTERNAME
c:\ProgramData\CustomScripts\Get-WindowsAutoPilotInfo.ps1 -OutputFile \\servernaam\autopilot$\csv\$pcname.csv
Out-File -FilePath $(Join-Path $env:ProgramData CustomScripts\start.ps1) -Encoding unicode -Force -InputObject $start -Confirm:$false
Out-File -FilePath $(Join-Path $env:ProgramData CustomScripts\reset.ps1) -Encoding unicode -Force -InputObject $reset -Confirm:$false
#Sysinternals download part
invoke-webrequest -uri: “https://download.sysinternals.com/files/SysinternalsSuite.zip” -outfile “c:\programdata\customscripts\pstools.zip” | out-null
Expand-Archive c:\programdata\customscripts\pstools.zip -DestinationPath c:\programdata\customscripts\pstools -force | out-null
Start-Process powershell -ArgumentList '-noprofile -file c:\programdata\customscripts\start.ps1'
Step 3. Creating a GPO and create some Tasks
So, we have these 2 scripts. What do we do with them? We got 2 options:
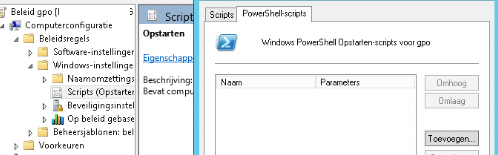
First one: Computer Assigned PowerShell script:
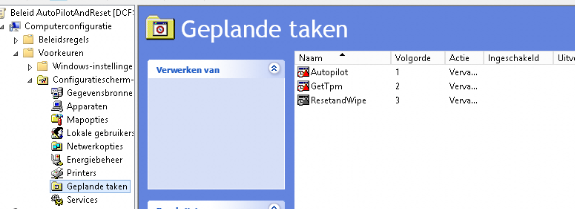
Second one: (my favourite) and the one I will be talking about: computer assigned tasks.
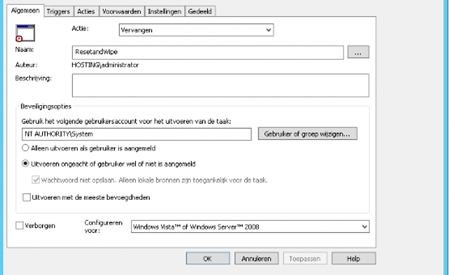
You can simply, configure the PowerShell scripts above to run as “System”
Let’s try it out to see what happens and if it works as you should expect.
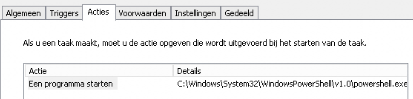
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
-NoProfile -ExecutionPolicy Bypass -File c:\windows\temp\reset.ps1
As I showed above, I made sure the PowerShell scripts are already on the device itself. You can do this, by creating a file computer GPO policy. Inside this gpo you can configure some rules to copy some files to your device
4. DoWipeProtectedMethod
First Tips: keep the reset and wipe task disabled until you’re 100% sure you have all the hashes and you are ready to enrol all your devices within Intune!!!!
Second Tip: combine the csv’s to save some time or automate the process!
Third Tip Please take a look at this setting:
$methodName = “doWipeMethod”
You can change it to DoWipeProtectedmethod
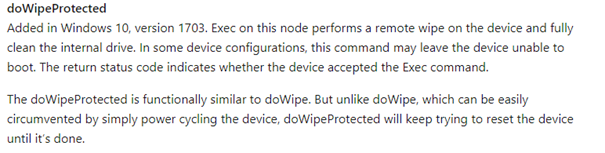
“The doWipeProtected is functionally similar to doWipe. But unlike doWipe, which can be easily circumvented by simply power cycling the device, doWipeProtected will keep trying to reset the device until it’s done.”
But when you have some Microsoft Surfaces you would like to enroll with Autopilot, please use dowipemethod. As you have read above: The surface will end up in a non-bootable state because it doesn’t have a WINRE
Conclusion:
Automate where you can, manually reinstalling your devices is not necessary when you have implemented this solution. It can really save you some time when transforming to a zero-trust modern workplace.


One thought on “Remote Wipe: The Next level”