My second blog in just one day, but sometimes you get scared as hell! Today at 13:00 AppLocker suddenly began blocking the famous psscriptpolicytest files on all our 2019 Remote desktop servers. That’s very weird behaviour. Why on earth is this happening at the same time on all our 2019 servers? You almost feel like you need to prevent the collapse of the western civilization… no pressure.
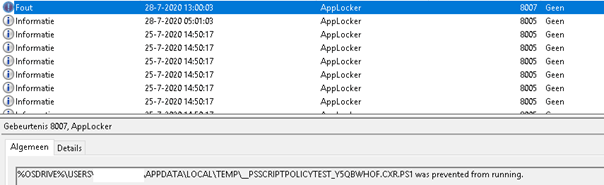
We are using Solarwinds as part of our SIEM (more on this subject on my next blog). That means a lot of tickets about Applocker and Powershell warnings at our SOC.
It’s time for some investigation. We investigated all the logs we got: Applocker/Security (with all options configured)/Windows defender/PowerShell.
The PowerShell operational log showed us that PowerShell suddenly started an IPC listening session. These sessions were started from a regular user account (we definitely don’t allow users to start PowerShell) That’s not just weird anymore…. That’s very strange indeed.
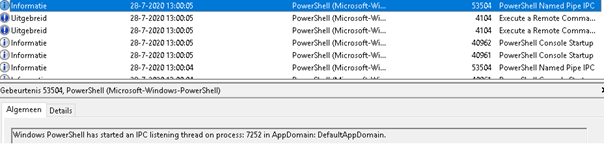
So why only the 2019 servers? Why not the other 2016 remote desktop servers? In my next blog I’ll tell you why you need SYSMON. I guess, this is already is a good example! Let’s open the Sysmon event log.
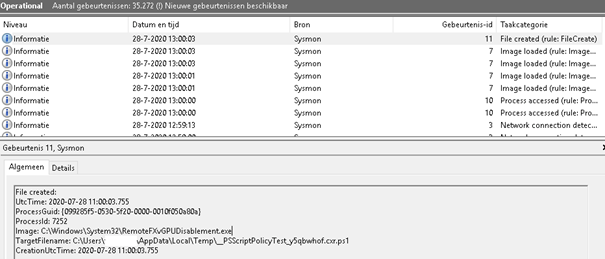
Remotefxgpudisablement. Okay? I’ve heard the announcement, remotefx will be disabled in the feature. I guess this is a kind of check. I could not find any info about It, anywhere…
It appeared like a new scheduled task. And yes, it was. Every 30 days on 13:00 starting on 01-01-2014 and it runs for built in\users.
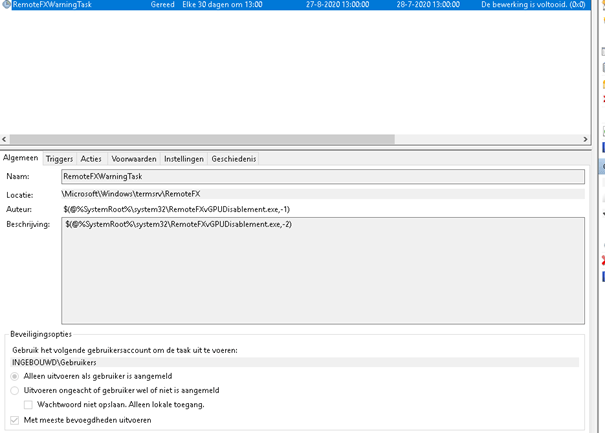
Conclusion:
Combining monitoring and a SOC is a necessity. So, if you have your AppLocker set up like me… You’ll know what to look out for.

