In this blog I’ll show you a new option to disable basic authentication protocols.
As most of you probably know, Microsoft is going to disable basic authentication for ActiveSync, PowerShell, Exchange Web Service, POP3, and IMAP4. You should especially disable POP3 and IMAP basic authentication as soon as possible.
Of course, implementing conditional access rules is the way to go. Read my other blog to learn how to automate your conditional access deployment.
When not having the proper licensing for conditional access, you could enable security defaults.
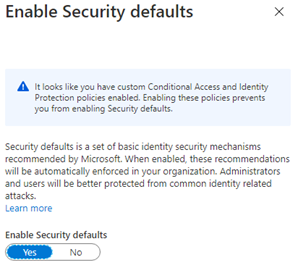
But security defaults have it flaws. You can’t make any exclusions! A break glass account may come in handy someday and having one won’t be possible if you use security defaults. It’s very weird Microsoft recommends using an emergency account but won’t allow you to make exclusions in the security defaults.
So, what other options do we have to disable the basic authentication protocols?
1.Configuring your CASMailboxPlan to completely disable POP and IMAP
Get-CASMailboxPlan | Set-CASMailboxPlan -ImapEnabled $false -PopEnabled $false
This will disable POP and IMAP on a tenant level, but won’t disable it for existing mailboxes. Luckily, we have another command:
Get-CASMailbox -Filter {ImapEnabled -eq "true" -or PopEnabled -eq "true" } | Select-Object @{n = "Identity"; e = {$_.SamAccountName}} | Set-CASMailbox -ImapEnabled $false -PopEnabled $false
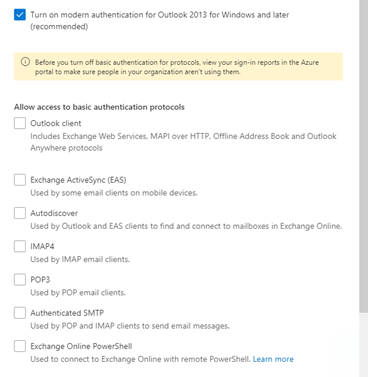
2. Configure Modern Authentication within the Microsoft 365 Admin center. (UPDATE 14:00. Microsoft has pulled back this update so it seems)
Look at all these new options!
3. If you want to automate the process, use PowerShell to create a new authentication policy after you set up a PowerShell session to exchange online:
new-authenticationpolicy -name "BlockBasicAuth"
$policy = get-authenticationpolicy
$policyname = $policy.name
$policyid = $policy.id
set-authenticationpolicy -id $policyid -AllowBasicAuthActiveSync:$False -AllowBasicAuthPop:$false -AllowBasicAuthSmtp:$false -AllowBasicAuthImap: $false -AllowBasicAuthMapi:$false -AllowBasicAuthWebservices:$false -AllowBasicAuthPowershell:$true -AllowBasicAuthAutodiscover:$true(You can check your settings with get-authenticationpolicy)
When your authentication policy is created you can assign it to specific users or just everyone with no authentication policy assigned.
Get-user -Filter {Authenticationpolicy -eq $null} | Set-user -authenticationpolicy $policyid
Conclusion:
So, do you allow basic authentication? Are you crazy, you don’t allow basic authentication!
Don’t forget to block the basic authentication protocols. Conditional access is by far the best solution. But there are some other options in case you don’t have the proper licenses.

