This blog will be about my experience performing a remote wipe of Windows 10 and 11 devices in Intune. I noticed some weird and awful behavior when remote wiping these devices.
Please Note: If you want to skip the introduction and just want to know how to “fix” it…for now: Part 7!
1.Introduction
Before I am going to show you the differences between remote wiping a Windows 10 device and a Windows 11 device I need to give you a little introduction to Remote Wiping a device in Intune.
I wrote a blog post some time ago about all the remote options in Intune for wiping, refreshing, or resetting a device.
Imagine the day you receive a Phone call from a CFO for a company you work for. She tells you, she just received her brand new notebook and wanted to pass her old device (almost brand new) to her colleague.
Luckily, she is using OneDrive with Known Folder Move activated, so setting up her old notebook is going to be a piece of cake. But what about her old device?
This company is located a couple of 100 miles away so sending someone in to reimage the device was a no-go at this time. But as explained in the blog above we have multiple options to perform a remote wipe.
So you decide to perform a remote wipe to make sure the device is wiped clean!
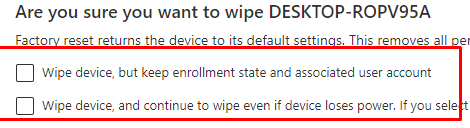
As shown above, when performing a remote wipe you will be prompted with multiple options. Let me explain them a little bit more.
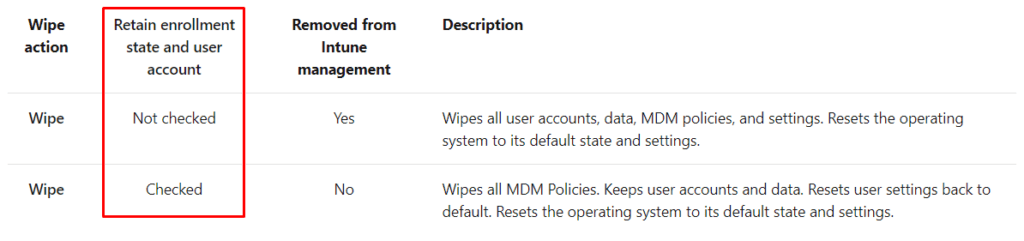
So what happens when we DIDN’T select anything and DIDN’T select the option to retain enrollment and the user data? Microsoft is telling us:
“All data, apps and settings will be removed”
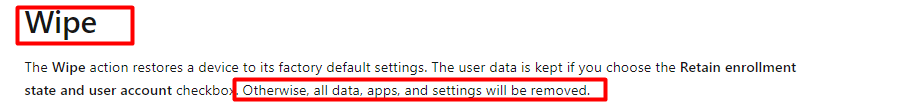
We made sure we didn’t select anything, so let me show you what happened! I will also show you the differences between performing a remote wipe on Windows 10 and Windows 11.
2. Remote Wiping Windows 10 21H1
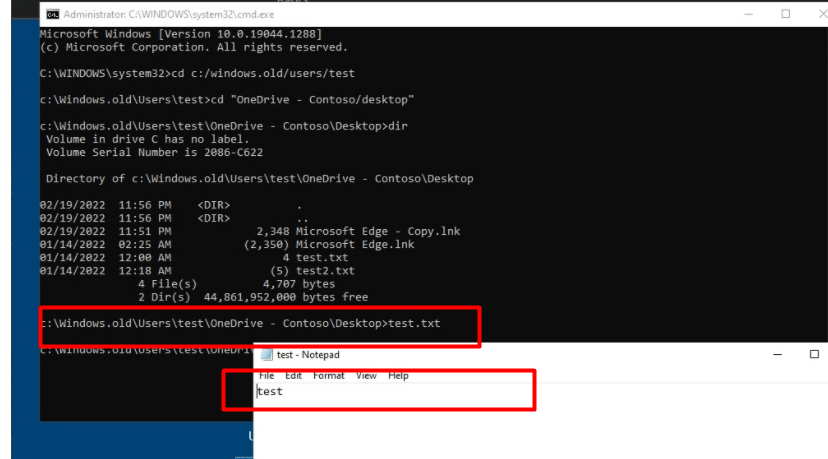
When performing a remote wipe from Intune on a Windows 10 21H1 device and we don’t select the retain data option, your device will be reinstalled and “wiped” as expected. After looking at what’s left on the hard disk we will notice it is no longer encrypted with Bitlocker. Also, we could notice a Windows.old folder in the root. Luckily, this folder is very empty after performing a remote wipe from Intune on a Windows 10 device!
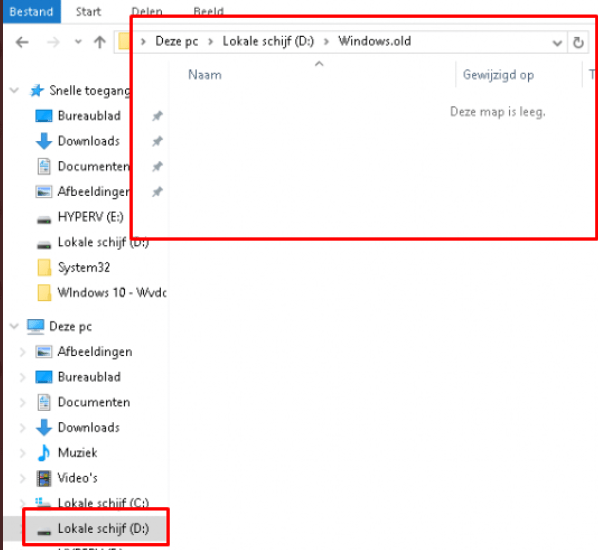
Looking at the picture above, that is what you expect to happen when performing a remote WIPE!
3.Remote Wiping Windows 11
However, the device in question was installed with Windows 11. So what happens when we execute the same Remote Wipe from Intune on a Windows 11 device? We will notice something different! Of course, we are making sure we don’t select the option to retain the user data option

I will divide this part into multiple subparts because I wanted to know what happens when performing a Remote Wipe on a Windows 11 VM in different kinds of situations. Each time the Virtual Machine was 100% done enrolling with Bitlocker
3.2 Using Shift+F10 at the sign-in screen
3.3 Wipe device, and continue to wipe….. AKA DoWipeProtected
3.1. Locally opening the VHDX
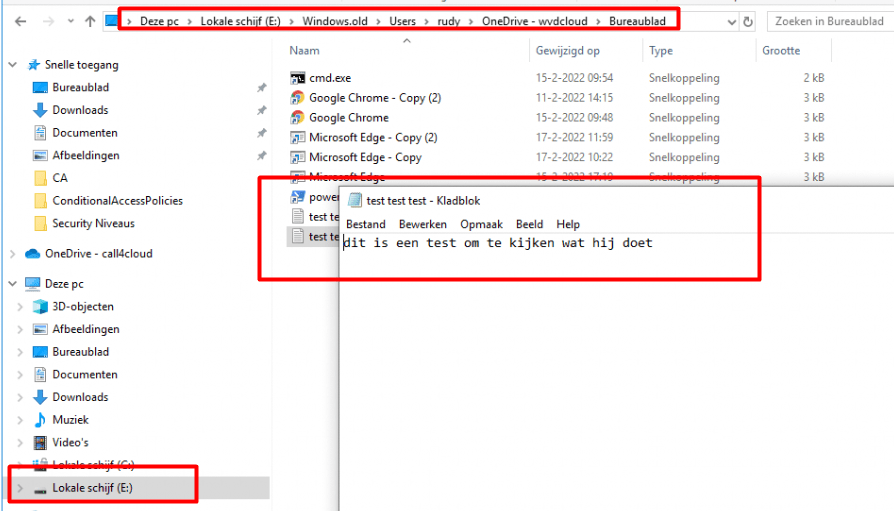
After wiping the device, which was installed with Windows 11, 21H2 and previously encrypted with Bitlocker, we noticed that the old personal user data folder was moved to Windows. Old folder. But that’s not a big deal if BitLocker is still enabled. We all know what happens when we perform a remote wipe of the device. Bitlocker protection is also removed! So, we end up with some sensitive data on a non-encrypted hard Disk?
Let’s take a look first at how it looks when we mount the VHDX from a VM in which I tested this Remote Wipe. I am opening this VHDX from my HyperV 2016 test server
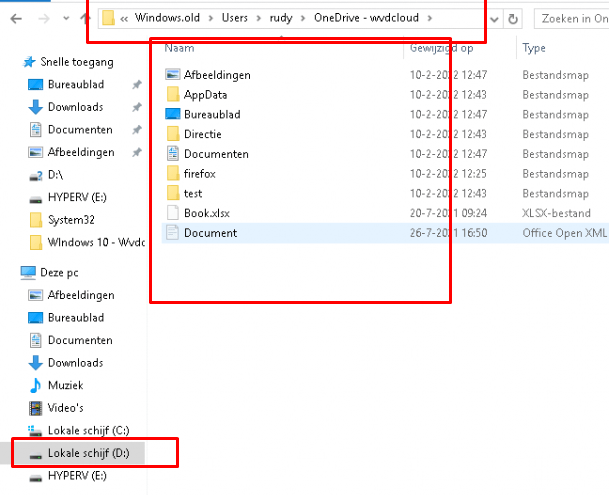
As shown above… in the Windows.In the old folder, is there still old user data with all our OneDrive KFM data left in it? I guess the warning that Microsoft gives us: “This removes all personal and company data and settings from this device” is not totally true with Windows 11“
But let’s find out if we are able to open those files? Because having those files still on the device is 1 but having the possibility to open it is 2.
With this first attempt, it really looked like the files couldn’t be opened because copying gave use the error: 0x80070780
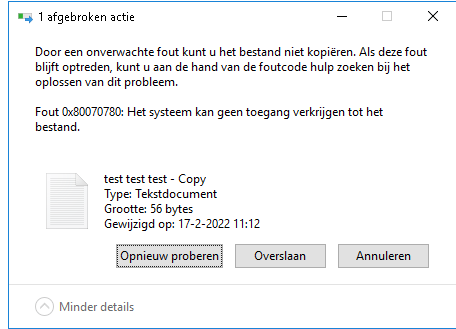
Opening the file gave us this message: “The System couldn’t get access to the file”
But I am not done yet, let’s see what happens when we fire up the VM itself and start opening the file with the use of Shift+F10 at the login screen or just attach the VHDX to a different VM.
3.2. Using Shift+F10 at the sign in screen
Let’s continue because the errors I got when locally opening the VHDX were a little bit weird in my opinion. Of course, I took over the permissions. But I didn’t trust the outcome!
So I wanted to see what happens when we performed a Remote wipe on a device that was previously Bitlocker Enabled and just used Shift+f10 to get a system CMD?
As shown below. *It’s possible to open all of the files!!!! How the hell should that be possible? I am wiping the device and choosing to NOT retain data!!!!!, so why is there still sensitive data on it?
*Please note: When using OneDrive Files on-demand functionality, only the files that are marked as “Always Keep on this device” are accessible. Otherwise, you could end up with 0 kb files

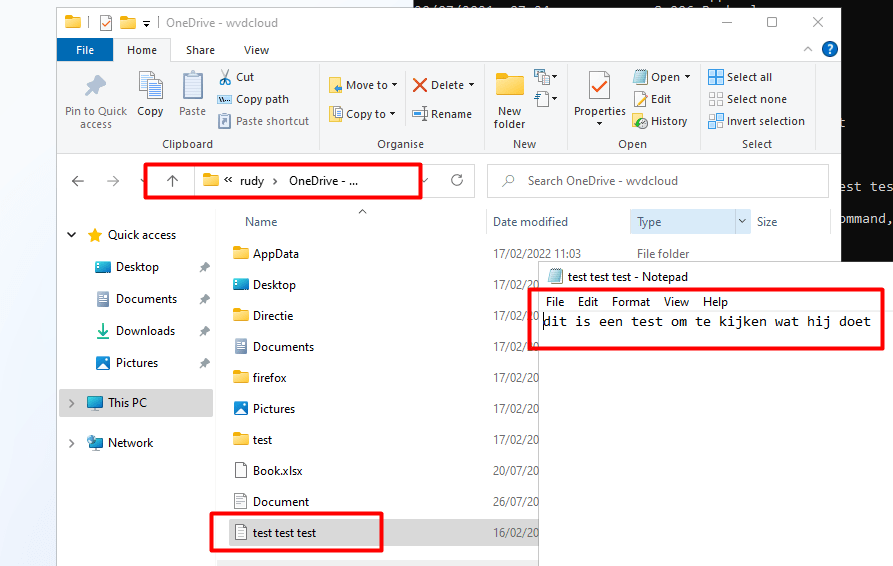
Also attaching the VHDX to another VM I had on that same Hyper-V server gives us the possibility to open those files!!!! That’s very very very bad! we can copy that sensitive information to our own device!
3.3 “Wipe device, and continue to wipe…..AKA DoWipeProtected”
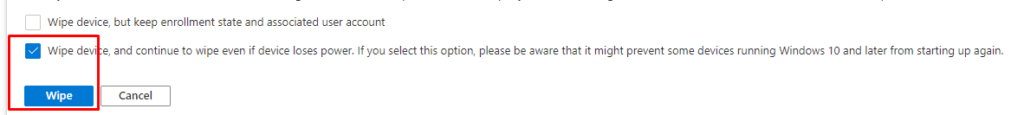
Philip Cumiskey asked me what would happen when selecting the bottom checkbox: “Wipe device, even continue to wipe if the device loses power” aka DoWipeProtected Method.
Actually, that was a very good question as I didn’t test it yet. Looking at those options, the actual difference between selecting the bottom checkbox and not selecting it would be choosing between DoWipeMethod and DoWipeProtectedMethod.
Some time ago I created a PowerShell script to wipe your device without Intune… and I explained the DoWipeProtectedMethod in it
But let’s continue and take a look at what happens when we select the bottom option to start the remote wipe!
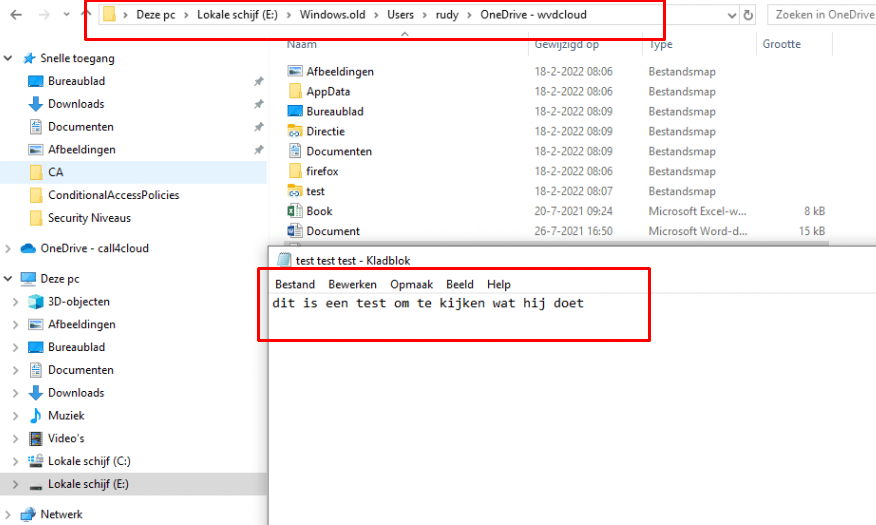
You can guess what happened… Just like with the DoWipeMethod… the windows.old folder is still there and the data is also readable from a different VM
4.Remote Wiping Windows 10 21H2
Okay, so when performing a remote wipe, Windows 21H1 wipes the device just like we expect but Windows 11 totally screws things up! I still wanted to know what happens with an up-to-date Windows 10 21H2 build. I made sure I downloaded the latest 21H2 Windows 10 build and started the whole enroll and wipe process again.
As shown below, even with the latest Windows 10 Build, sensitive data is left when performing a remote wipe! That’s pretty awful because at first, I thought this issue only affected Windows 11 devices.
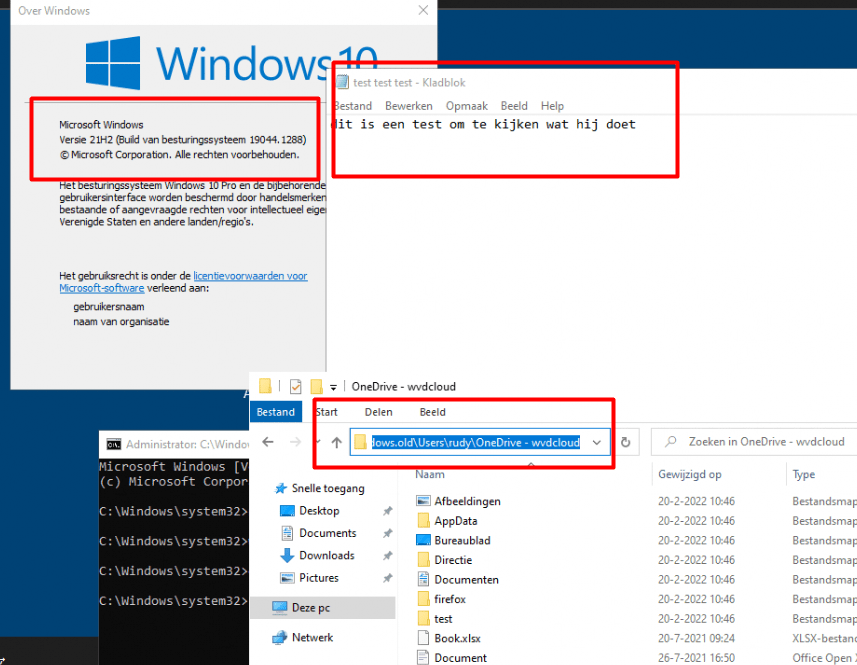
Please Note: This issue is only occurring when you have a fresh installed Windows 10 21H2 device! When your device is upgraded from 21H1 to 21H2 the folder is removed! Strange?
5. Wiping a not Enrolled Windows 10 21H2 Device
Remote wiping a Windows 10 21H2 or Windows 11 device will leave some sensitive data on the device, but what happens when we enroll a new stand-alone/unenrolled VM and just perform a local wipe?
When resetting your local PC, you have 2 options, as shown below. Of course, we will choose “Remove Everything” to be sure everything is removed, right?
I guess it’s pretty obvious, even when performing a local wipe on a Windows 10 21H2 device it will leave the user data in the Windows.old folder… this is worse than I thought at first!
Alena also did a test drive with the “Cloud Download” option
You could guess the outcome by now!!
6. The Complete Summary
The Wipe functionality (DoWipe and DoWipeProtected methods) has the same issue in Windows 10 21H2 and Windows 11 when performing a local or remote wipe or even a Fresh Start. All of them just trigger the DoWipeMethod, and when using OneDrive and offline files, you are up for a challenge!
| Action | Results |
| Remote Wipe 21H2 | User Data NOT removed from Windows.old |
| Remote Protected Wipe 21H2 | User Data NOT removed from Windows.old |
| Local Wipe 21H2 | User Data NOT removed from Windows.old |
| Local Wipe Cloud Download 21H2 | User Data NOT removed from Windows.old |
| Local Protected Wipe 21H2 | User Data NOT removed from Windows.old |
| Remote Fresh Start 21H2 | User Data NOT removed from Windows.old |
| All Wipe /Fresh Start actions with 21H1 | User data REMOVED from Windows.old |
| Upgraded Windows 10 21H1 to 21H2 | User data REMOVED from Windows.old |
So it’s definitely NOT an Intune Issue, it looks like something changed in the 21H2 update with the DoWipeMethod and in combination with OneDrive and its Mount Points/Reparse Points!
Please note: I am not saying the “wipe” option is the safest or the best option out there but when Microsoft Docs is telling us the data will be removed you would expect all of the data to be “wiped/removed“.
This issue only occurs when you are using OneDrive (tested it with the Production and Deferred Ring) and of course, you need to have been signed in at some point. Also when using files on demand, it’s pretty obvious when the file isn’t on the device it can’t be opened from the Windows.old folder!
If you are interested in the technical flow behind this remote wipe, you should definitely read part 2!
7. The Fix?
Just after posting the first version of this blog, I realized we could solve this weird issue just like I did with the Shift+F10 Nightmare. In this blog, I used the resetconfig.xml to configure Windows Recovery Environment (Windows RE) Push-button reset features
Please download the whole PowerShell Script to fix the Windows 11 Remote Wipe Nightmare!
https://call4cloud.nl/wp-content/uploads/2022/02/RemoveWindowsold.zip
8. Explaining the Fix
Before I show you what I changed in the PowerShell script, I need to explain what happens when “Wiping” your device and the Extensibility Points
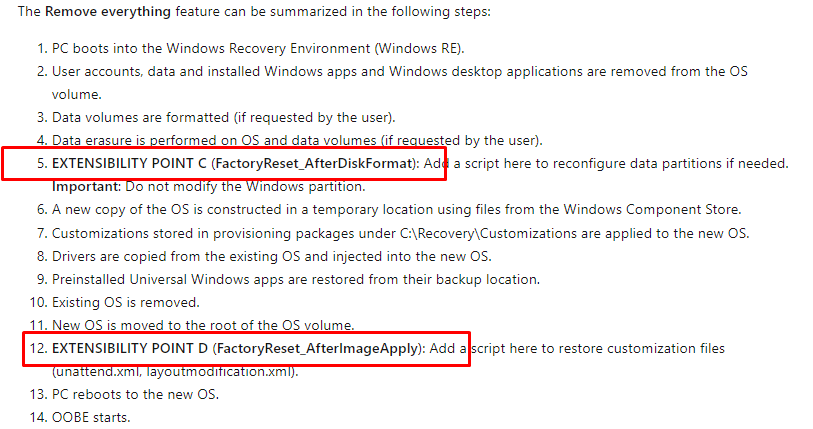
As shown above, we have 2 Extensibility Points to choose from, “FactoryReset_AfterDiskFormat” and “FactoryReset_AfterImageApply” when we want to apply some additional configuration.
Looking at the resetconfig.xml that is created in the PowerShell script, you will notice it will be executed after applying the Image.
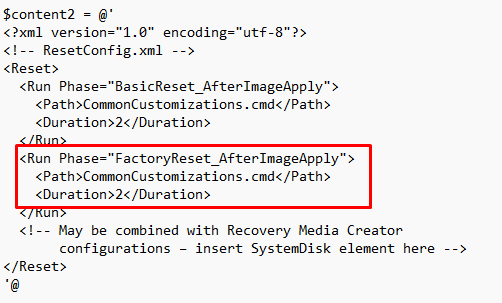
Of course, it would be better it would run FactoryReset_AfterDiskFormat but at that point in time the Windows.Old folder is not yet restored (even while we don’t want to retain data!). Believe me, I tried.
Now we know what the resetconfig.xml looks like, let us take a look at the PowerShell script itself. Comparing it with the Shift+F10 version, the only adjustment I made, was adding: rmdir /s /q c:\windows.old\users. I guess you know what it is going to do!
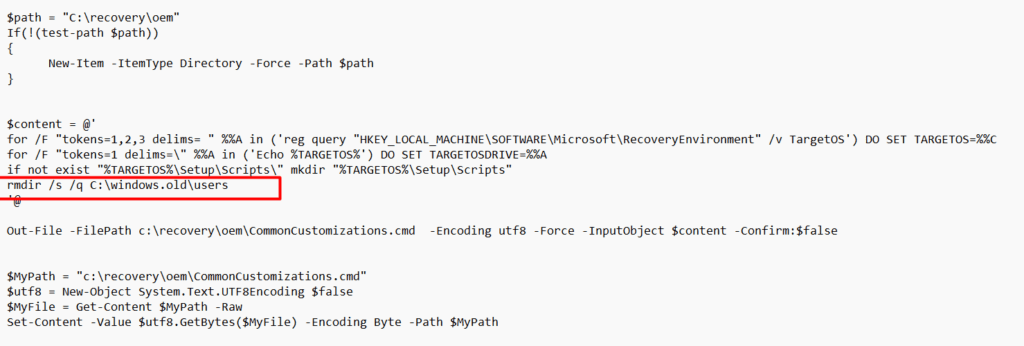
After you made sure this PowerShell script is deployed to your devices you can wipe your devices and the evil Windows.old folder is also removed. As there is no spoon…. uhhh folder, it’s hard to show you, but you know what I mean.
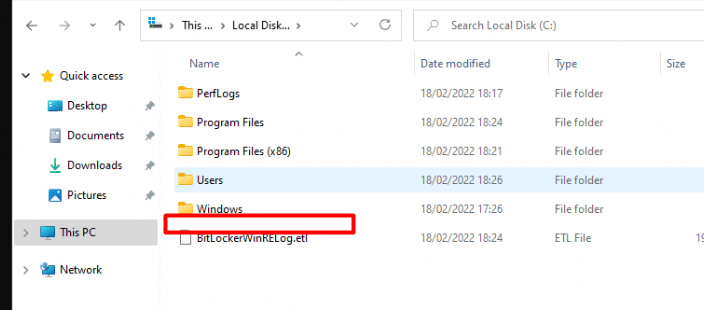
Please Note: I am writing an additional blog about the “wipe” option itself, it will explain how fragile this “wipe” function is….even with Windows 21H1! If it sounds secure, it has to be secure…. right?
9. Windows.Old folder and Windows 8.1
Why on earth is there still sensitive OneDrive data on it after a “Wipe” without selecting the retaining data option? Of course, I tagged the Intune Support Team to get some response.
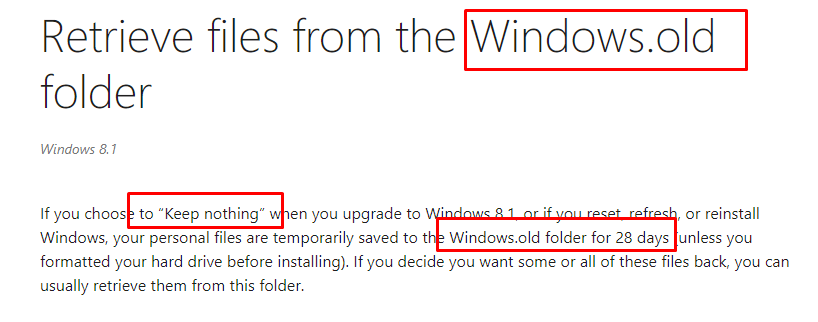
Again… this is not what we want!!!! we don’t want a disk cleanup to delete that folder after 10 days!. Is Microsoft referring to the Windows 8.1 good old days 🙂 ?
Retrieve files from the Windows.old folder (microsoft.com)
Please Note: Microsoft isn’t ignoring us or this issue!!! They are working hard to provide a fix as soon as possible. Hopefully, Microsoft will release this fix very very soon! I will keep this blog up to date when stuff changes!
10. IT336291
Today I noticed a new Incident in the service health and message center: IT336291. It’s telling us some “users may notice some files persisting after resetting a Windows Device“
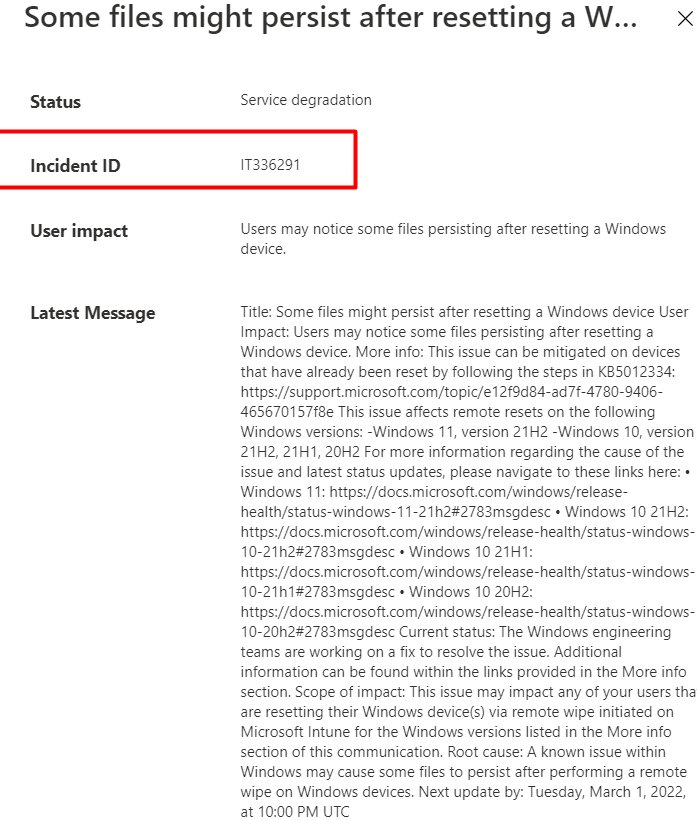
Looking at the above incident, it is telling us to take a look KB5012334
https://support.microsoft.com/topic/e12f9d84-ad7f-4780-9406-465670157f8e?id=5004252
And this article:
These articles are showing us some pre and post solutions.
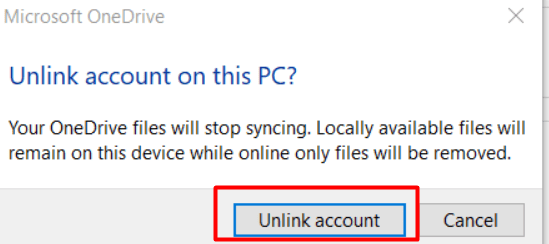
Pre Solution:
Unlink the OneDrive Account before Wiping the device to ensure it doesn’t end up in the Windows.Old folder after the wipe!
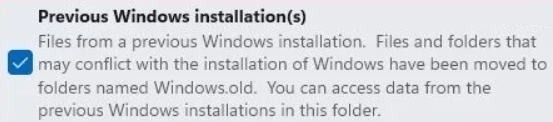
Post Solution:
Remove the windows.old folder ourselves by opening settings –> system –> storage
But I guess my fix works a little bit more automated… because normally (when not using Shift+f10) you would need to log in after your device has been wiped to remove this folder manually. But what happens when you log in with your username on a device whose 4k HH hash was uploaded to Intune? Indeed… When configured, OneDrive would launch and start syncing your files back to your device!!.. Sound like a Chicken or the Egg situation?
11. KB5011493 and KB5011487
Luckily Microsoft released their official fix in the March Updates, KB5011493, and KB5011487. I decided to dedicate a separate blog to these updates as they do deserve a blog on their own!
Conclusion:
Maybe I am too critical at this point and maybe I am getting “Banned”….

But ….Microsoft is telling us “Otherwise, All data will be removed” as shown below
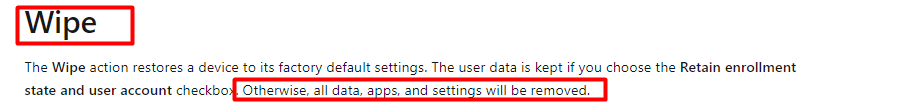
Retire or wipe devices using Microsoft Intune | Microsoft Docs
The contents of that folder shouldn’t even be there in the first place! So please make sure when performing a remote wipe on a device before you hand it over to someone else please remove that folder manually...or use my fix until Microsoft deployed the fix.
p.s: I only wrote this blog to create some awareness about this issue…Not to speak evil 🙂


Hi Rudy, may i know when do i run the ps script. Is it before running the wipe or after running the wipe?
Hi, good morning. The PowerShell script needs to be run before the wipe… As it makes sure the winre is configured to remove that folder after the wipe. So when using Intune you could simply push out this script to all of your devices
When you are wiping them it will use the resetconfig.xml inside the recovery\oem folder to. In this XML the rmdir is configured to remove the windows.old folder
Has a ticket been opened with Microsoft.
They need to know about it if this is a bug. Otherwise it’s not going to get fixed.
Let me say… they are pretty much aware and yes multiple tickets have been opened by multiple people but opening another one couldn’t hurt!
Awesome research. Thank you. I reposted immediately.
You can also reimage locally with diskpart. I find that to be the most reliable way, imho.
https://www.linkedin.com/posts/activity-6902227165153484801-PTTU
oops meant to say wipe but was unable to edit.
some links in the TOC are mixed up or wrong: “part 2” does not work at all. “part 4” opens a link to “part4” in a new tab. “part 7” links to “part 6”.
Thanx.. Just fixed it.. I guess adding parts screwed up the layout a little bit 🙂
Hi, what happens when you download the 21h2 installation media and try it with that one?
If you find other vulnerabilities like this in the future, you may consider reporting them to https://msrc.microsoft.com/. They have a sizable bug bounty program and this likely would have qualified.
Hi, i know :)… a year ago it got me 20k. But intune isnt in the scope
Hi, Kb5011493 (Win11) und Kb5011487 (Win10) seem to address the issue and are currently rolling out as March Updates.
They “should” indeed 😛 Did you check out my latest blog?
Are the files in the windows.old folder securely deleted? Since there are files there that were once encrypted, and are no longer encrypted – when the system deletes them, are they securely erased?
It depends on whats your opinion about secure 🙂 .. With the latest KB from march Microsoft will also remove that folder using a resetconfig.xml (just like I did) so that folder is removed/deleted before the decryption. I am not saying you cant recover them afterwards…. 😛
Would a wipe with “clean this drive” checked securely remove that data after the update and make it tough to recover?
Hi, as repleyed on a another question… the lingering data is still there after selecting clean this drive
Also, how could the uodae erase it before it’s unencrypted if it could take up to 7 days after the reset while the data is sitting there in the folder unencrypted?
Is this only the case for enterprise versions of windows 10/11 or all?
Hi, The update only makes sure the WUT task will be launched with 1 week. By doing so the resetconfig.xml is placed which makes sure when the device will be reset the windows.old folder is removed. You can speed it up like I am mentioning in this additional blog
https://call4cloud.nl/2022/03/before-we-wipe/
To add to my previous question – if updated to the latest March update, then reset, would that have taken care of the file before the “clean drive” reset or could it be persistent after the reset with the recent update(the up to 7 days part) and then deleted in which case it would still be on the drive? At what point is it deleted before decryption?
Hi, I am explaining the whole flow in this additional blog. But the removal will happen at FactoryReset_AfterImageApply just before the decryption (98%) then device reboot to start the safe os phase
https://call4cloud.nl/2022/03/ill-always-know-what-you-did-last-wipe/
Thank you again for the information! So after the reset (and before the update kicks in) and the unencrypted windows.old file is sitting on the drive, will that information get encrypted again or will it live on the drive unencrypted forever since I believe most modern PC encryption just encrypts used data, not the entire drive anymore? Does the windows “clean data: clean the drive” pass the whole drive over with 1’s and 0’s?
Basically how do you make this windows.old file reasonably unrecoverable?
It depends… after you reset the device… you could use shift f10 to access that unencrypted data… The best way to make sure your the data isn’t recoverable will be in an upcoming blog
Looking forward to it!
Does the erase the drive option, not just wiping/removing the files, affect the outcome or prevent the files from being put into windows.old?
If it leaves lingering unencrypted data on the drive forever, that seems a bit issue
It will erase the whole drive… but while doing so also the WINRE… so reinstalling windows in that same flow is a no go.. This method should be used when you want to remotely ditch the device.
1. Just to clarify, if reset this pc-> remove everything->cloud download -> change settings -> clean data (clean the drive) and download windows set to yes -> confirm on windows 10/11 won’t have this windows.old persistent user data issue?
2. If you sign in again after reset, will it re encrypted the windows.old folder on the c drive of the ssd?
1) –> still has that windows.old\user folder… 🙂
2) –> if you sign in and you have configured bitlocker, that folder will be indeed encrypted.. but you could always use shift+f10 before logging in
Ah, okay thank you for clearing that up!
So after sign in, and the folder is encrypted after bitlocler is set up, then shift + f10 will no longer work after boot once user is back in with their account?
Also, what happens to the unencrypted data after it is re-encrypted upon sign-in? Is there an in encrypted copy, or does bitlocker somehow protect it ?
I had the same issue before with disappearing files. I used Stellar Data Recovery, and it easily recovered everything I lost. I’d suggest trying it if you’re facing the same problem.
Hello,
Thank you for this great job.
I just tested it and it’s OK.
My goal is to wipe our computers before reselling them to our users.
So I would like to add 2 steps:
Step1: Create a local admin account
–> I added these commands in the $content variable
net user “XXX” YYYYY /add
net localgroup administrateurs “XXX” /add
echo ok > c:\test.txt
this last command is to check if the script was executed.
In the end, my test.txt file is there but not the XXX account: Maybe an issue with the doublequote or it should not be done in that phase of the OS deployment ? What do you think ?
Step 2:
Disconnect the computer from Entra: “dsgregcmd /leave” I think ?
Thank you for all your articles. I really appreciate them.