Last Updated on March 23, 2022 by rudyooms
Today I realized I totally forgot to add this setting to my App protection baseline. Let’s talk a little bit more about this wonderful new setting “Conditional Launch” that was released some months ago.
I will divide this blog into multiple parts
it’s very easy to configure, just open your App protection policy and configure the conditional launch setting within your app protection policy.
1. Conditional Launch
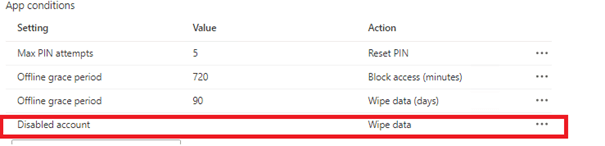
When looking at the actions available, you have got 2 options:
Block access: When Intune has confirmed the user has been disabled in Azure Active Directory, the app blocks access to work or school data.
Wipe data: When Intune has confirmed the user has been disabled in Azure Active Directory, the app will perform a selective wipe of the user his work or school account and data.
In my opinion, it is very important you configure this setting. If you don’t configure this setting and you forgot to retire or wipe the device the user could still access the data in an offline manner until the offline grace period wipe timer has expired.
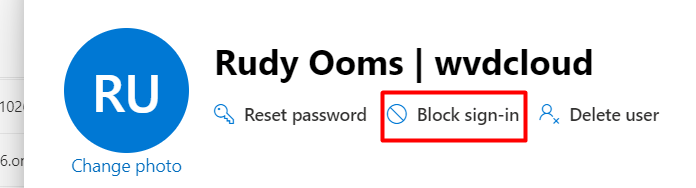
How could we Block/Disable the user instead of deleting the user? You could disable the user by configuring “Block Sign-in” in the user properties at the Microsoft Admin Center
https://admin.microsoft.com/Adminportal/Home#/users/
2. A few important notes:
1: This does not work, when you chose to immediately delete the user instead of disabling it. When you delete the user, the user has still access to the data in an offline manner until the Offline Grace Period wipe timer has expired.
2: There are several things that could impact the time to initiate the wipe, like if you are running azure ad connect/ azure ad access token (120 minutes) and the Intune app check-in time (30 minutes)
3. When the user has been blocked access, the user will not be able to access the org data. But please beware that any new data can still be delivered in the background because the access tokens will not expire, but luckily the user wouldn’t have access to it.
3. PowerShell Automation
Of course, you can change this setting manually but why not automate it for new deployments?
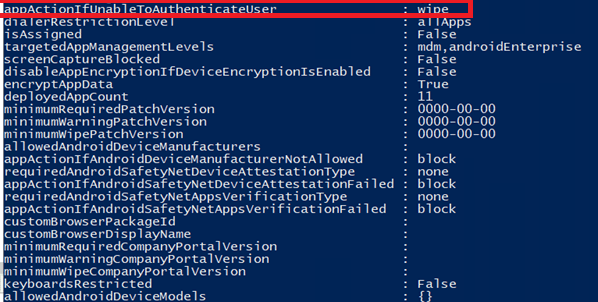
You could also make sure you configure this setting in your App Protection baseline by configuring the: “appactionifunabletoauthenticateuser” like I am showing below
Check my website for the PowerShell scripts
The Chronicles of MAM – Call4Cloud Setting up IOS App protection policies
Conclusion:
When combining App protection conditional Launch with continuous access evaluation, you will get the best result. CAE will make sure the user will be blocked almost instantly and the app protection policy will make sure the company data is wiped.


Hi Rudy,
Thanks for the explanation. When you adjust ‘appActionIfUnableToAuthenticateUser’ to wipe, block (or warn!) you will see this in the GUI as ‘Disabled account = …’.
This implies that the action is solely for a disabled account, while the Microsoft documentation says: ‘If set, it will specify what action to take in the case where the user is unable to checkin because their authentication token is invalid. This happens when the user is deleted or disabled in AAD. Inherited from managedAppProtection. Possible values are: block, wipe, warn.’ (Source: https://docs.microsoft.com/it-it/graph/api/intune-mam-defaultmanagedappprotection-create?view=graph-rest-beta).
They specify disabled ánd deleted. Did you already test if the wipe will also arrive when a user is deleted?
Hi, that part I didnt test if I am not mistaken.
“Important: The Disabled account setting does not detect account deletions. If an account is deleted, the user continues to access data in an offline manner until the Offline Grace Period wipe timer has expired.”
https://techcommunity.microsoft.com/t5/intune-customer-success/app-protection-policy-conditional-launch-improvements/ba-p/2209022?utm_source=dlvr.it&utm_medium=twitter
How do you disable a user in AzureAD?
Hi, good question… added it the blog
This feature doesn’t work at all. There is no indication when this will occur and you cannot set a time on this.
I’ve tested turning on this to “wipe.” Literally nothing happens until maybe 1 hour.
Offline grace period doesn’t refer to the user being disabled or deleted. It only refers to internet access. So if the device never loses internet access, the offline grace period doesn’t apply.
When I was writing this blog, that feature was working… so if its not working for you… something must be wrong or Microsoft changes somethings