Securing your endpoints is essential to protect your systems from various security threats. This blog will walk you through the steps you need to take to ensure your endpoints are secure. We’ll cover everything from removing local admin rights to enabling essential security features. By following these straightforward steps, you can significantly improve the security of your Windows endpoints. Let’s get started.
But beware: Ensuring the users don’t have administrator permissions can cause problems. In this blog, I will show you how to deal with those.
Securing your device: Block Administrative Tools
You will need to prevent access to cmd and regedit. Please take a look at my blog to see how you can block these apps. You can even block Powershell!
Securing your device: Applocker
Nice… users are no longer admins. Why not implement a full Applocker policy? Using Applocker is great when you, of course, need to block Powershell
If you want to be sure PowerShell and some other LOLBINS are blocked, please deploy this Applocker baseline
Securing your device: Bitlocker
Make sure you enable Bitlocker. You can do this through the Intune portal or a custom-built Intunewin app based on a PowerShell script. Your choice…
Important Note:
BitLocker automatic device encryption initiates during the Out-of-box (OOBE) experience. However, the encryption protection is fully enabled (armed) only after the user signs in with a Microsoft Account or an Azure Active Directory account. Until that point, the protection remains suspended, and data is not secured. BitLocker automatic device encryption will not activate automatically if the user signs in with a local account. In such cases, BitLocker must be manually enabled through the BitLocker Control Panel.
Changes to Automatic Device Encryption in Windows 11 Version 24H2
Beginning with Windows 11 version 24H2, Microsoft has lowered the hardware requirements for Automatic Device Encryption (Auto-DE) in Windows:
- Auto-DE no longer relies on the Hardware Security Test Interface (HSTI) or Modern Standby.
- Auto-DE will be activated even if untrusted Direct Memory Access (DMA) buses or interfaces are detected.
Securing your device:: Windows Defender with ASR rules
Please turn on Windows Defender and configure the ASR Rules. You can automate the deployment as I did with the Applocker policy.
And please when you have money to spare, enable Microsoft Defender for Endpoints (ATP)
Securing your device: Security Baseline policies
Take a look at the baseline policies in Intune. They are easy to implement, and if you’d like to dig a little deeper, you can create your own baseline with a PowerShell script. I find it easier to read than the baseline policy, and not all security configs exist in the Intune baseline policy.
#Harden lsass to help protect against credential dumping (mimikatz) and audit lsass access requests
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RunAsPPL /t REG_DWORD /d 00000001 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest" /v UseLogonCredential /t REG_DWORD /d 0 /f
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation" /v AllowProtectedCreds /t REG_DWORD /d 1 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LSASS.exe" /v AuditLevel /t REG_DWORD /d 00000008 /f
#Disables DNS multicast
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient" /v EnableMulticast /t REG_DWORD /d 0 /f
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient" /v DisableSmartNameResolution /t REG_DWORD /d 1 /f
#Disable anonymous access to named pipes/shared, anonymous enumeration of SAM accounts, non-admin remote access to SAM
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v TokenLeakDetectDelaySecs /t REG_DWORD /d 30 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RestrictAnonymousSAM /t REG_DWORD /d 1 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RestrictAnonymous /t REG_DWORD /d 1 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RestrictRemoteSAM /t REG_SZ /d "O:BAG:BAD:(A;;RC;;;BA)" /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v LmCompatibilityLevel /t REG_DWORD /d 5 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v LimitBlankPasswordUse /t REG_DWORD /d 1 /f
#Enable PowerShell Logging
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging" /v EnableScriptBlockLogging /t REG_DWORD /d 1 /f
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\PowerShell\ModuleLogging" /v EnableModuleLogging /t REG_DWORD /d 1 /f
#Disable autorun/autoplay on all drives
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\Explorer" /v NoAutoplayfornonVolume /t REG_DWORD /d 1 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer" /v NoDriveTypeAutoRun /t REG_DWORD /d 255 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v NoAutorun /t REG_DWORD /d 1 /f
#Enable And lock down firewall
new-item -Path 'HKLM:\SOFTWARE\Policies\Microsoft' -name "WindowsFirewall"
new-item -Path 'HKLM:\SOFTWARE\Policies\Microsoft\WindowsFirewall' -name "DomainProfile"
new-item -Path 'HKLM:\SOFTWARE\Policies\Microsoft\WindowsFirewall' -name "PublicProfile"
new-item -Path 'HKLM:\SOFTWARE\Policies\Microsoft\WindowsFirewall' -name "StandardProfile"
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile' -name "EnableFirewall" -Value 1
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\WindowsFirewall\PublicProfile' -name "EnableFirewall" -Value 1
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\WindowsFirewall\StandardProfile' -name "EnableFirewall" -Value 1
Auditpol /set /category:"System" /SubCategory:"Filtering Platform Packet Drop" /success:enable /failure:enable
Auditpol /set /category:"System" /SubCategory:"Filtering Platform Connection" /success:enable /failure:enable
#Removing Powershell.20
Disable-WindowsOptionalFeature -Online -FeatureName MicrosoftWindowsPowerShellV2RootSecuring your device: Windows Firewall
Turning on the Windows Firewall is always a good thing. You could configure it with Intune. I dedicated a blog about this some time ago!
Securing your device: Windows Hello or MFA Authenticator
It’s straightforward to turn on MFA and Windows Hello… I recommend requiring users to use at least a device PIN instead of their password.
If you want to read more about credential providers and how to use the Microsoft Authenticator for Windows logon:
https://call4cloud.nl/2021/04/battle-for-the-planet-of-the-web-signin-providers/
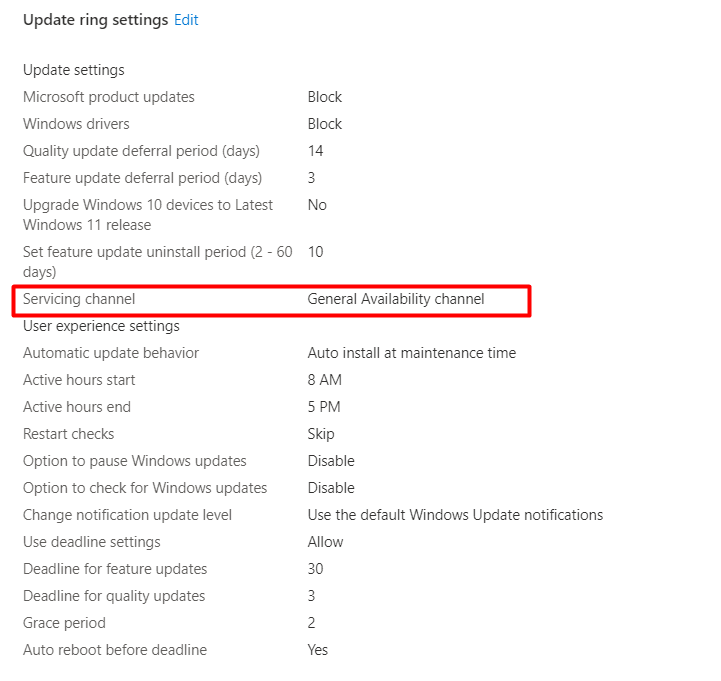
Securing your device: Windows Update
Windows has to be kept up to date; go configure Windows Update for Business (WHfB) within Intune. Please beware of the servicing channel. You could configure it specifically to use the Insider Slow, but for production environments, it’s not the best option, so I made sure I selected the “general availability channel”
Securing your device: Office 365 Apps Security
Don’t forget about the macro’s and file type settings in Office. If like me, you didn’t know why blocking DIF and Sylk files is necessary. Take a look at this blog from Outflank https://outflank.nl/blog/2019/10/30/abusing-the-sylk-file-format/. They do a very good job of explaining why this is important.
You can block these file types in the settings catalog
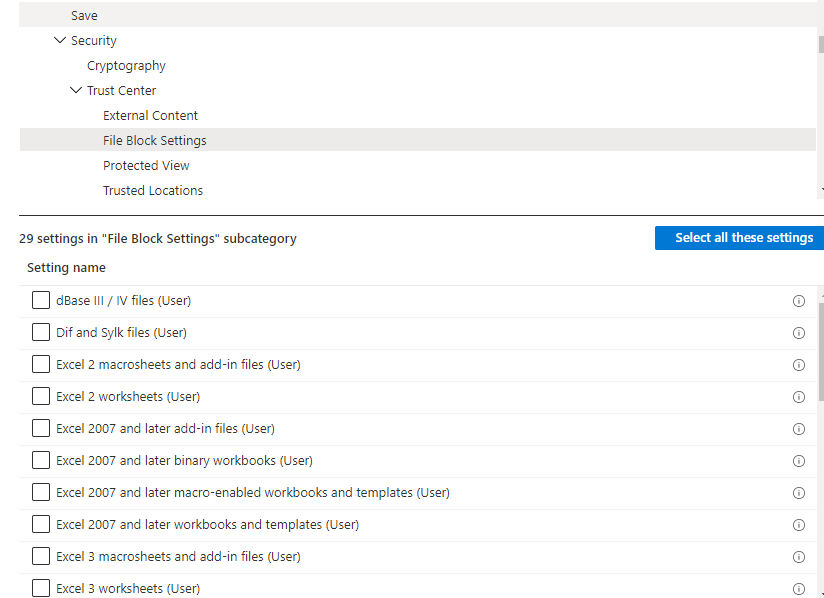
Of course, I also created a blog about this topic. Go read it if you want to know more.
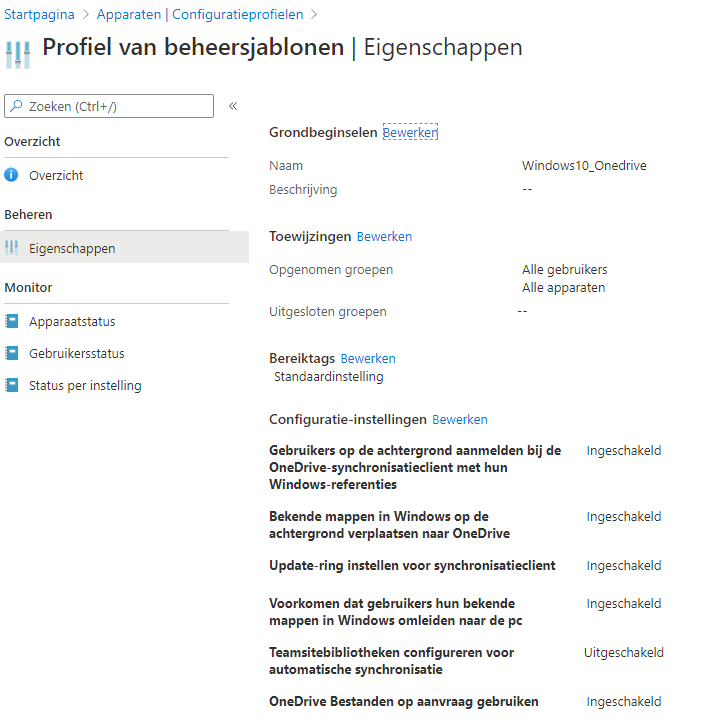
Securing your device: OneDrive KFM
OneDrive KFM is a nice solution for silently redirecting documents and desktops to your OneDrive account. It also protects your data against ransomware.
Securing your device: Chocolatey or Winget
Have you considered patching third-party apps? Use Chocolatey (or Winget… but it does not have an automatic upgrade function). It’s very good…, and your third-party apps will be up to date forever.
Invoke-Expression ((New-Object net.webclient).DownloadString('https://chocolatey.org/install.ps1')) -ErrorAction Stop
$ChocoPackages = @(“jre8”,"adobereader","7zip.install")
$chocoinstall = Get-Command -Name 'choco' -ErrorAction SilentlyContinue -WarningAction SilentlyContinue | Select-Object -ExpandProperty Source
foreach($Package in $ChocoPackages) {
try {
Invoke-Expression “cmd.exe /c $ChocoInstall Install $Package -y” -ErrorAction Stop
}
catch {
Throw “Failed to install $Package”
}
}
##Create A scheduled task to Update all packages each day at 12:00
choco install choco-upgrade-all-at --params "'/DAILY:yes /TIME:12:00 /ABORTTIME:14:00'" -yIf you want to know how you could do the same with winget:
Securing your device: Audit Logging
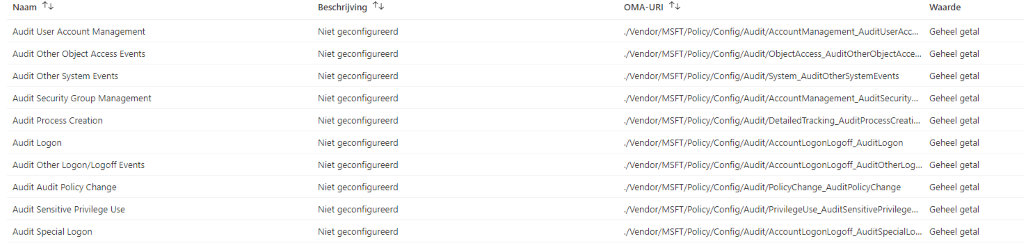
Did you increase the Security/System/Application event log size? Please make sure that you have configured auditing and that you have the proper licensing set up.
/Vendor/MSFT/Policy/Config/Audit/
Policy CSP – Audit – Windows Client Management | Microsoft Docs
Securing your device: LAPS
Have you thought about implementing LAPS? In these 2 blogs below I will show you the possible options on how to configure a sort of LAPS
Securing your device. MCAS
Microsoft Cloud App Security is a fantastic product. You really want to have it deployed and active in your Microsoft 365 Tenant. I wrote a blog on how to set it up and automate some of its steps.
Conclusion:
You have to take a few steps… but your endpoints need to be secure. Configuring all these settings in your tenant can be much work. Guess what? All these steps can be done within a few seconds.



