Looking back at my blogs, I realized I didn’t tell you the whole story concerning restricting user access to the Azure AD portal.
Last night I was talking to Nicola Suter about this and he made me realize there are some additional steps you can take to further improve security.
- Preventing access to the Azure AD Portal itself should be the first step. But there are more ways an attacker can get the information stored here. The attacker can open a PowerShell prompt and run: Get-msoluser to get all user and group information within Azure AD. You can prevent this by changing the UsersPermissionToReadOtherUsersEnabled setting: Set-MsolCompanySettings -UsersPermissionToReadOtherUsersEnabled $false
Beware! Disabling this setting will break the option for users to add new members to Teams. There’s actually a UserVoice submitted to Microsoft about this issue. Please vote for this (Microsoft really needs to change this).
Unfortunately, this doesn’t take away the possibility for an attacker to use get-msolgroup command. Currently, there’s no way to prevent this (that I know of).
- An attacker could still use Graph explorer to get the information within the Azure AD portal. Luckily, we can disable the Graph explorer app within Azure AD.
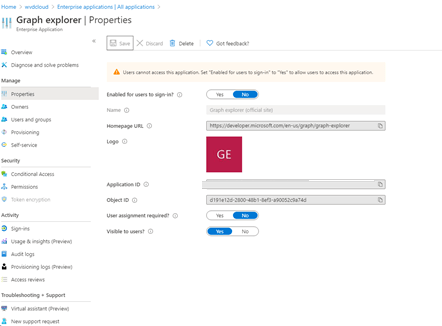
Beware! When you disable the app outright, no one can use the graph explorer. A better solution is setting the “user assignment required setting”. When you configure the setting like this, you can add the users that need to use Graph.
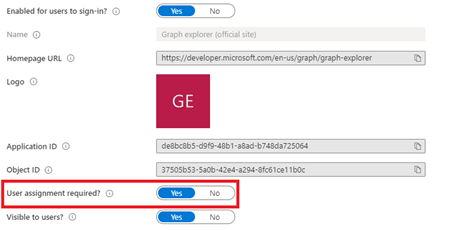
Conclusion:
We have to try to limit the attacker’s possibilities for getting the information within Azure AD as much as we can. Blocking / restricting these settings is the first step in creating a secure environment. But you’ll need to see the whole picture! It’s not only your tenant that needs to be secure, but also your devices. If you want to know more about this, please read my other blogs! I’ll teach you everything I know in these blogs.


One thought on “The Return of the Azure Ad Portal”