This blog will be about how to secure and harden your Office 365 Apps and maybe automate it with PowerShell.
Nowadays everyone should be securing their Microsoft 365 Tenant, their identity and the endpoints. Also, hardening your Office 365 apps is necessary because your devices are often targeted by malicious emails/websites.
I will divide this blog into 4 parts.
- Some background information
- Hardening Office365 Apps Manually
- Hardening Office365 Apps Automatically
- Application Guard for Office Apps
1.Background information
In one of my latest blogs, I pointed out the DIF and SYLK extensions but there is more, much more you could configure.
First, we need to take a look at what the Australian government has to say about hardening your Office 365 Apps
There are a lot of recommendations in it, but beware some of them can break stuff. As an example when you are configuring the AllowDDE setting you can end up with an error when your users want to open an existing excel file
“An error occurred when sending commands to the program” in Excel
So please make sure you take a real good look at each setting. When you need to do this for every customer you have, it could take up a lot of your time.
The Australian government is of course advising us to deploy ASR rules. Please visit my other blog about deploying the ASR Rules
2.Harden Office365 Manually
Of course, you can configure each setting manually:
Open Intune and create a new Administrative Template or configure it using the settings catalog.
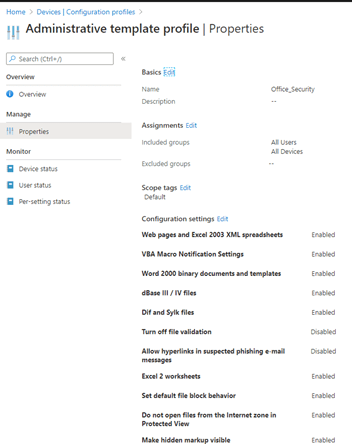
You can configure each setting by looking at the website I mentioned earlier
There are about +60 settings you’ll be able to configure, that’s a lot! Do I really need to configure all of this manually? Luckily we’re able to automate most of these settings.
3.Harden Office365 Automatically
When you need to configure it automatically, please download the zip file in the link below.
https://call4cloud.nl/wp-content/uploads/2020/06/office.zip
It contains a script with an ADMX folder with all the policies. Just run the PowerShell script as I show below.
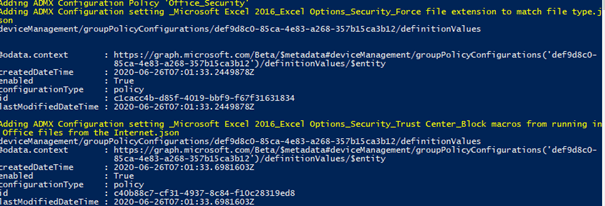
When you’ve run the script, you’ll notice a new administrative template has been created with all settings in the device configuration section.

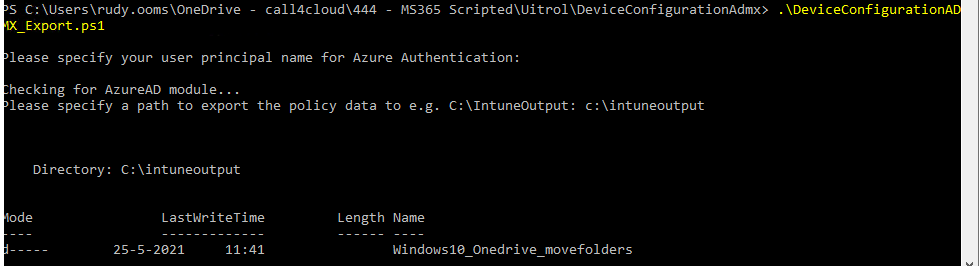
If you want to make your own version for the hardening of Office365, you will need to download this zip file
https://call4cloud.nl/wp-content/uploads/2021/05/DeviceConfigurationADMX_Export.zip
When running the script it will only prompt you for the location where the ADMX files need to be stored. Now you can use these files with the import script I showed you earlier.
I recommend testing out all of these settings before you deploy them in your production environment. As mentioned earlier, some settings can break your way of working.
4. Application Guard for Office Apps
Now we have hardened Office365 with some Intune settings we need to take a look at how we could improve the security a little bit more.
And that’s where the application guard for Office apps comes into place. Application Guard for Office Apps prevents untrusted files from accessing trusted resources.
You can configure this with one PowerShell script or Intune administrative templates.
Please take a look at my blog on how to enable this nice feature
Conclusion
Hardening your office 365 apps is necessary but can be a lot of work when you have to configure it manually on all your Office365 tenants. Luckily, we’re able to automate most of it and it’s really easy as well. Now go serve and protect!



Thanks for all the updated blogs, great work!
I have a question for you on Application Guard for Office which I’m struggling with and seems like an easy fix, or maybe not. I have two users, both on same tenant pretty much same Intune settings / Office policies across the board. User 1 creates a local word .doc or excel .xlsx, saves it to OneDrive. User 1 creates a new meeting in Outlook (M365 App) desktop app, attaches the file to the meeting and adds User 2 to the Invite. When User 2 opens the invite in Outlook desktop app, User 2 opens the attachment (doesn’t matter if the invite is accepted or not), the attachment runs in Application Guard every time when opening it within the invite.
If User 1 creates that file (trusted) inside the same tenant / domain, shouldn’t the document be trusted and not open in Application Guard? Obviously I could see this happening from an external invite or someone else internally who grabbed a documents off the internet.
Curious of your thoughts, thank you sir!
Hi,
Thanx..That’s indeed a difficult use case I will need to take a good look at and test it in my tenant. I will try to do so this week