Again, I am writing a blog about TPM attestation. Why? Sometimes, even when your device doesn’t have the Intel 11 gen or it isn’t an AMD device, you could still end up with some attestation errors during Autopilot for modern deployments.I guess today something broke at Microsoft ?
0x81039001 again – Microsoft TPM attestation service issues? : Intune (reddit.com)
So, I will create a separate blog to summarize the troubleshooting stuff I showed in the TPM attestation series
1. The 0x81039001 Error
First, let’s start with the issue that is occurring again today. We were (trying) to enroll 30 new Lenovo devices into Autopilot for pre-provisioned deployment.
Of course, we ensured we have the latest Win10 21h2 Build KB5007253, which fixes the Intel Tiger Lake attestation issue like I described in this blog.
But this time, the devices didn’t have a firmware-based Intel (11th gen), AMD, or Qualcomm TPM but one from Nuvoton! So we should expect no issues with that one, right?
Think again! We ended up with the error: TPM attestation failed! 0x81039001 !
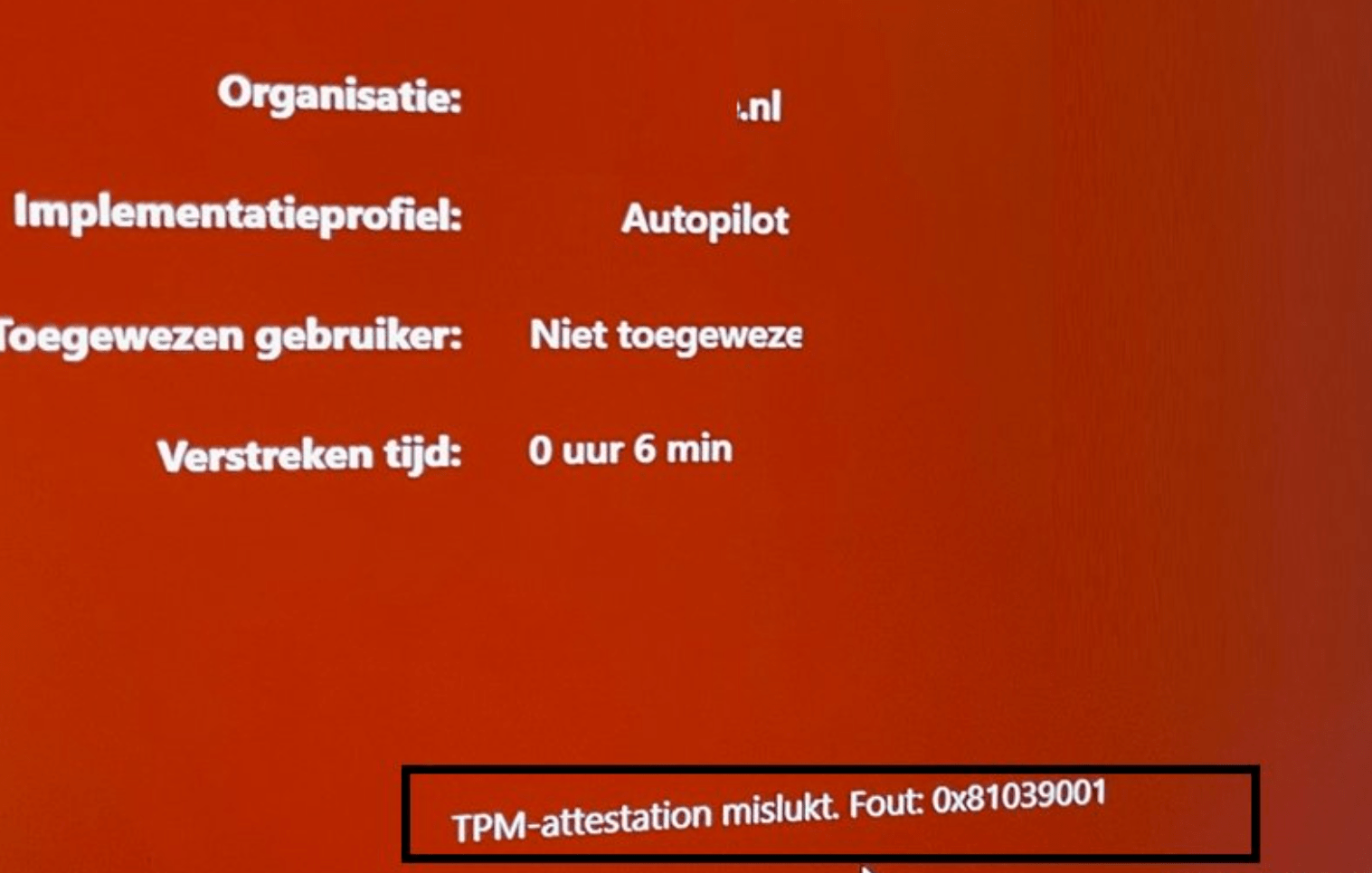
So, there are no deployments for us today, let me explain how to start troubleshooting
2. How to troubleshoot TPM Attestation issues
I already did some blogs about this topic… but let me summarize how you could detect what is going on.
2.1 TPMTool
Of course, we need to determine first if Attestation is even possible and if the device has the proper TPM version. To do so enter this command: TPMtool getdeviceinformation. This will give you a simple overview of the TPM capabilities
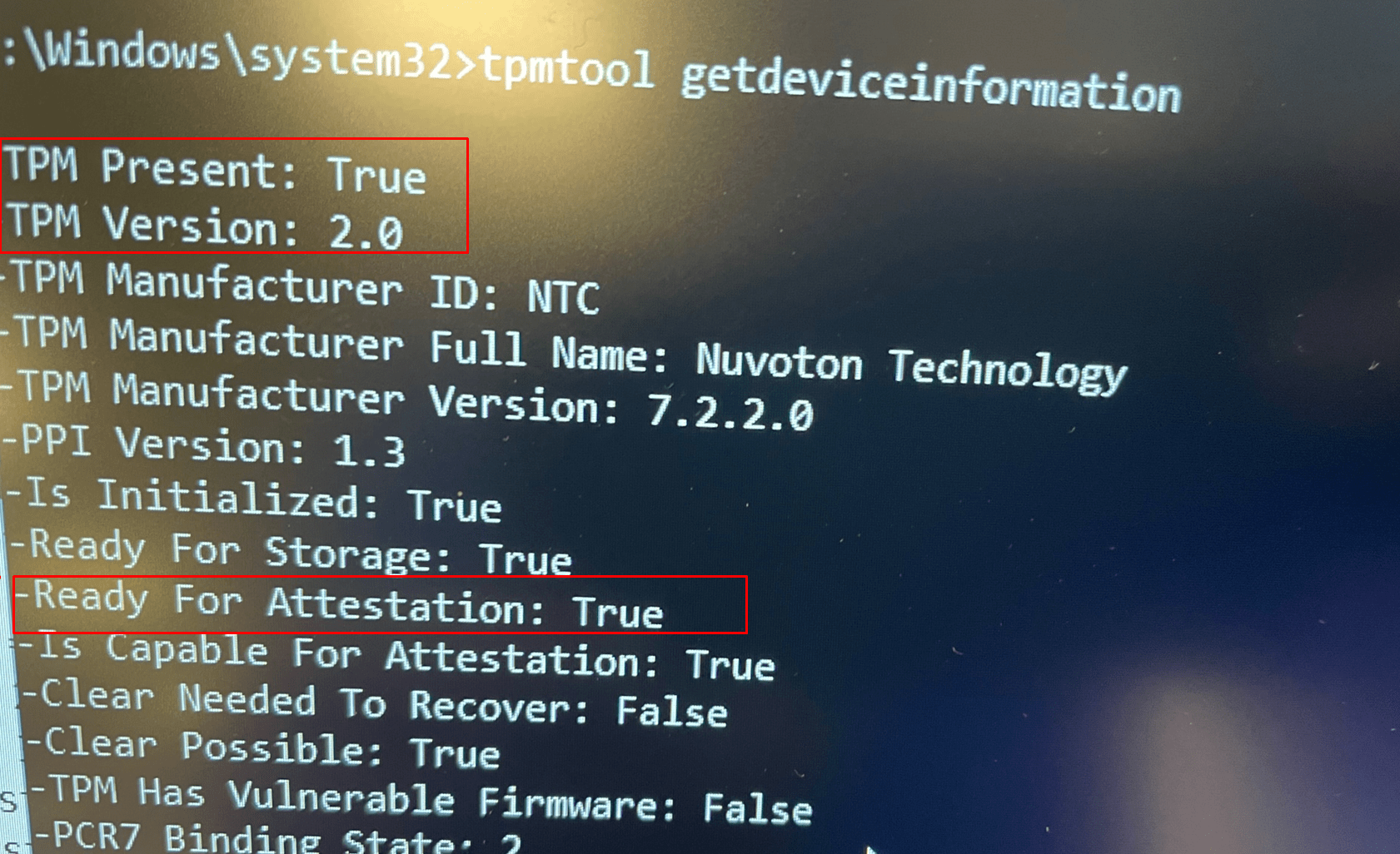
Now we are sure everything is good to go, let’s go forth!
2.2 Certreq
As shown in my other blogs, I am using the certreq tool to determine if it’s possible to start the AIK enrollment. So let’s start with that one by entering this command: certreq -enrollaik -config “”
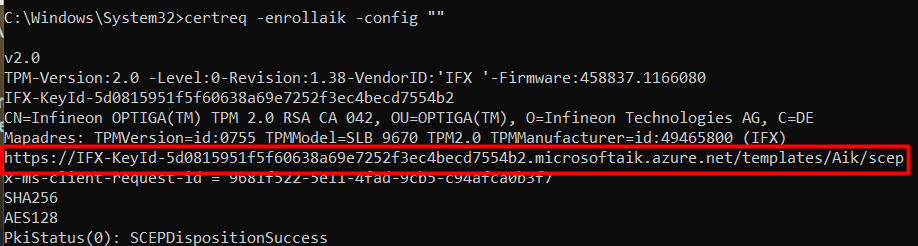
Take a look at the screenshot above. I am going to explain it some more. Normally It will show you the AIK enroll url it is using.
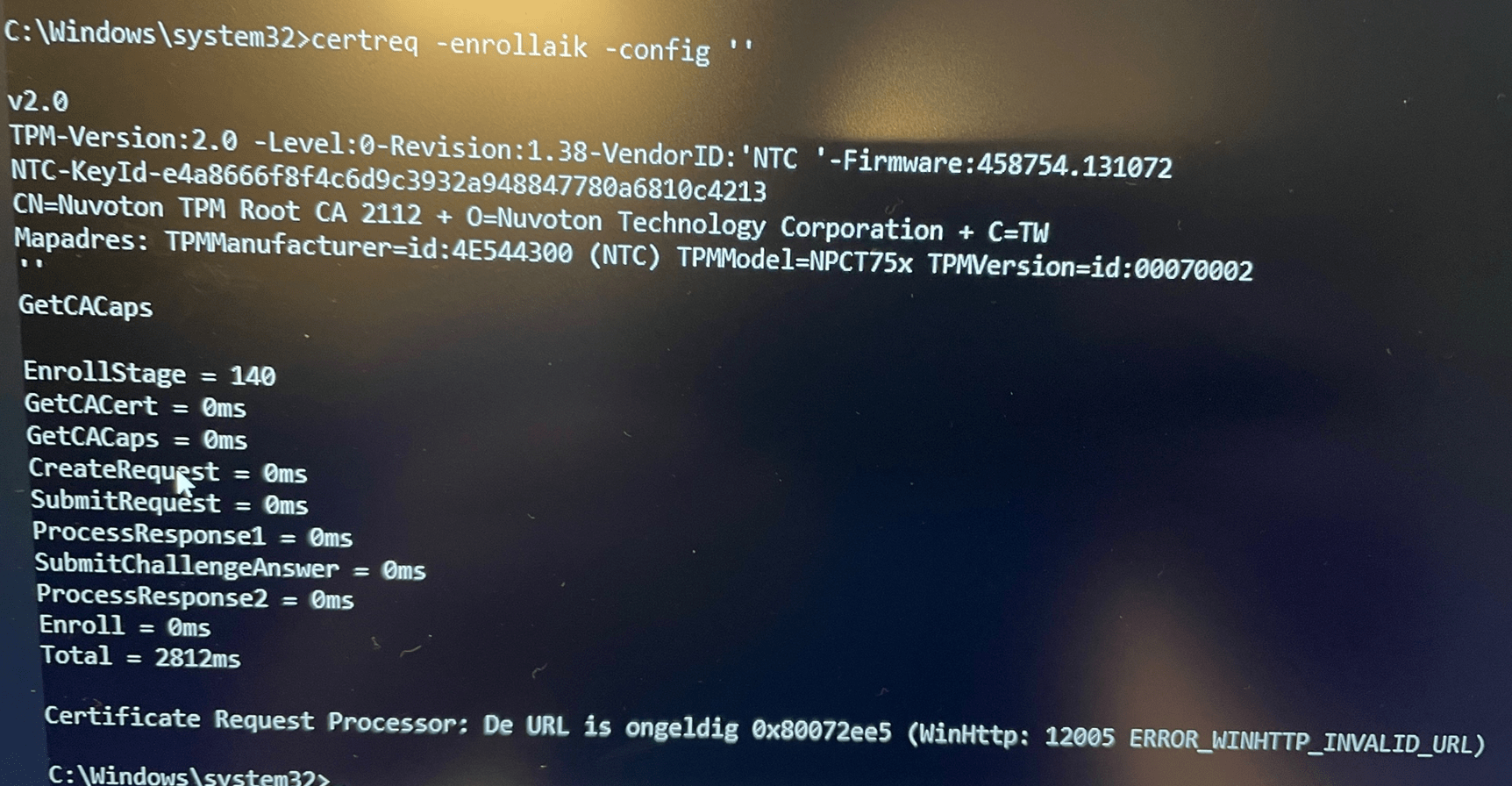
Please note: You need to enter the “” after -config, if you define something else (Like ”), the AIK attestation URL is not going to work! You will end up with a screen giving you the error: 0x80072ee5 (WinHttp: 12005 ERROR_WINHTTP_INVALID_URL)
2.3 TrustedTPM File
After running the certreq tool, we finally fetched the AIK URL. But we still need to check if the AIK URL is a valid one. To do so please download the trustedtpm.cab file from the Microsoft site

https://go.microsoft.com/fwlink/?linkid=2097925
Please note: In the screenshots above you could have noticed the NTC-KeyID .NTC (Nuvoton), INTC (Intel), AMD or STM (STMicroelectronics) are all just TPMS vendors. It depends on your hardware vendor which KeyId you will get.
When you have downloaded the file, extract and open the version.txt. Just simply search for the part after NTC-KeyId-.
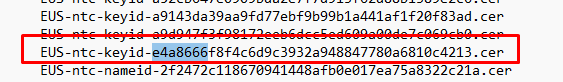
As shown above, it’s in the version.txt file.. so we can be sure the url is a valid one because that url is very important… if it’s not in the file…. AIK enrollment will fail!
Another important note to add: When you have found the AIK URL, please check if that AIK Cert is NOT “removed” as shown below!
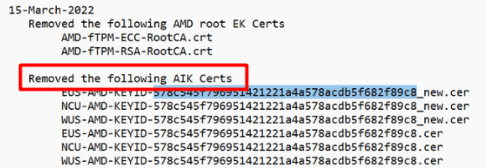
It looks like when Microsoft determines that somehow that AIK CA URL is used to deliver AIK certificates for vulnerable firmware versions, it will pull back that AIK URL even when it’s also used for not vulnerable firmware! In the example above, I guess Microsoft decided to shut down the AIK CA for that specific AMD fTPM .
When trying to re-enroll a previous working device with Autopilot for pre-provisioning deployments, you could run into this error: 0x800705b4 at the securing your hardware Phase when that AIK CA is withdrawn!
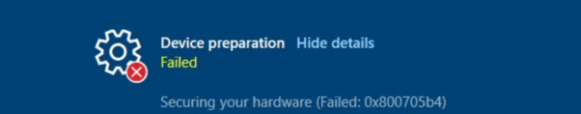
What we learned from this nice error: Even when it worked before, it doesn’t guarantee that it will work in the future!
2.4 Mdmdiagnosticstool
So when we do have a valid (not vulnerable) and working TPM and we know that the AIK enrollment url is fine so let’s get some more TPM information.
Enter this nice command to get the required information: mdmdiagnosticstool -area TPM -cab c:\temp\tpm.cab
Normally you won’t get an error… but this time… you can guess what is going to happen
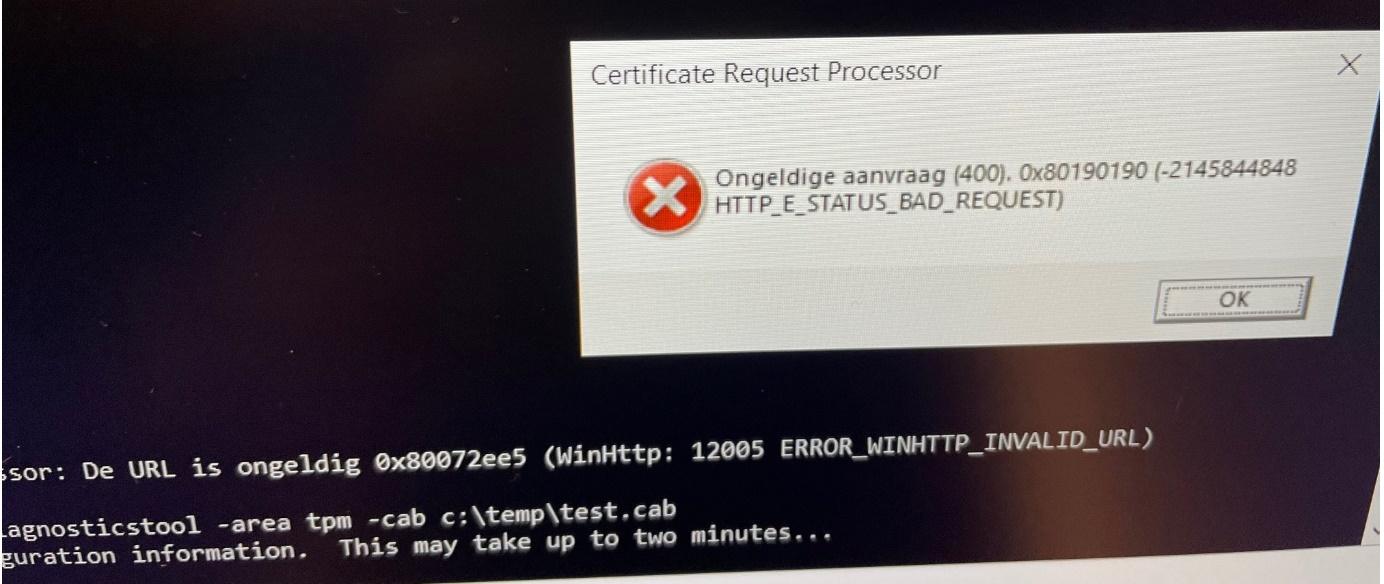
We are receiving 0x80190190 AKA -2145844848 error HTTP_E_STATUS_BAD_REQUEST. Luckily it will still create the cab file within in the certreq_enrollaik.txt file. Please open that one and search for errors!
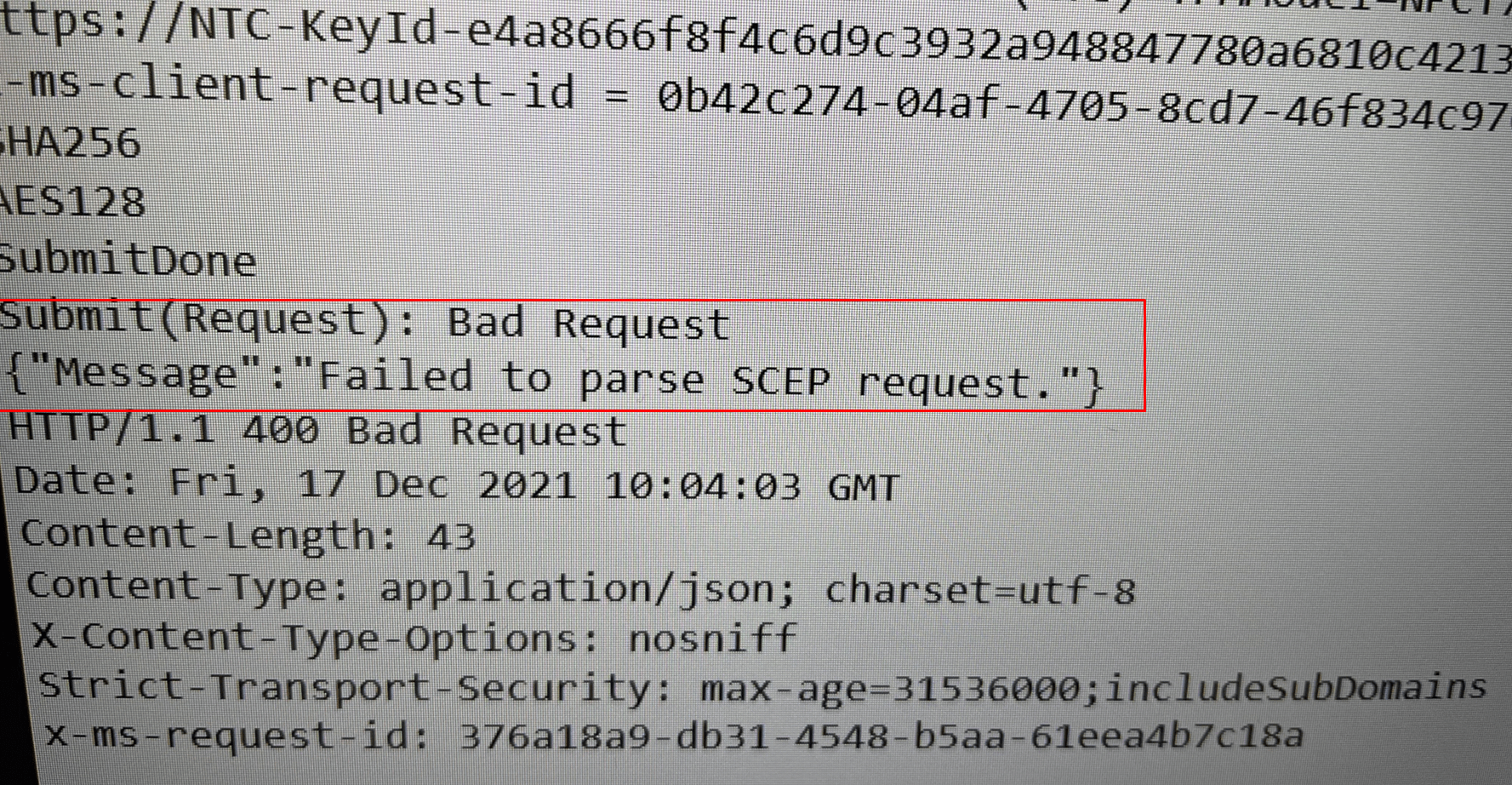
As shown above, we are prompted with the error: “Failed to parse SCEP request”. The error will tell us the Simple Certificate Enrollment Protocol request failed during the verification phase on the certificate registration point.
Normally, when everything is fine, you will notice the PkiStatus: SCEPDispotionSuccess. Sounds way better than the error we got
In this file, you will again notice the AIK url but as we know by now the AIK url isn’t the issue… let’s continue
2.5 Determining if the EK cert is available
When you have read my other blogs, you will know that the EK certificate (EKCert)is very important, if we don’t have the possibility to fetch that one and its intermediate certificate we could have a problem.
When you want to be sure you have a working EKcert, the easiest ways to check out if you have a working EK cert are these 2 options
*Registry
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tpm\WMI\Endorsement\EKCertStore\Certificates\
*get-tpmendorsementkeyinfo
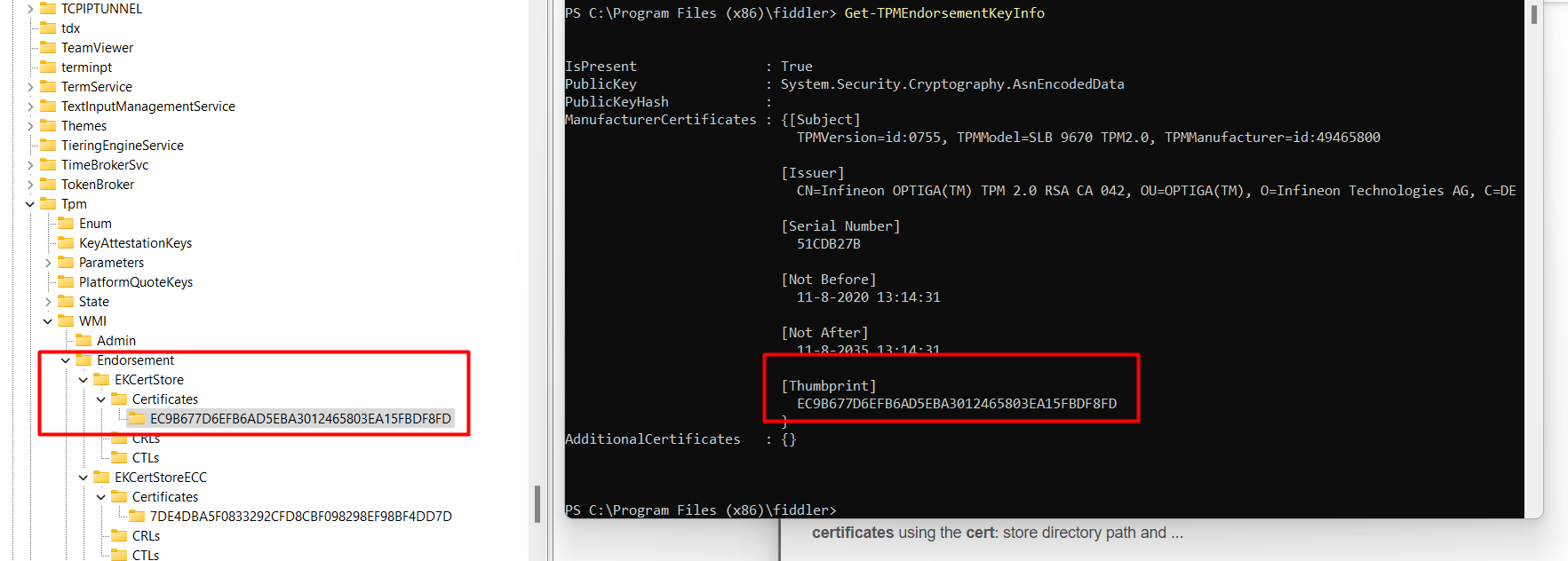
As shown above, we have got the requirements set up. No problems with the EKCert here!. After spending some time troubleshooting, I noticed on Twitter that a lot of people were suddenly experiencing TPM issues. So I decided to quit for today and start over tomorrow. And yes…!!! after a night of sleep, it was working!

2.6: Firmware
It sounds pretty obvious, but it’s also easily forgotten! When experiencing TPM attestation issues, it’s always, and I mean always!!! Best practice is to determine if there is new firmware available!
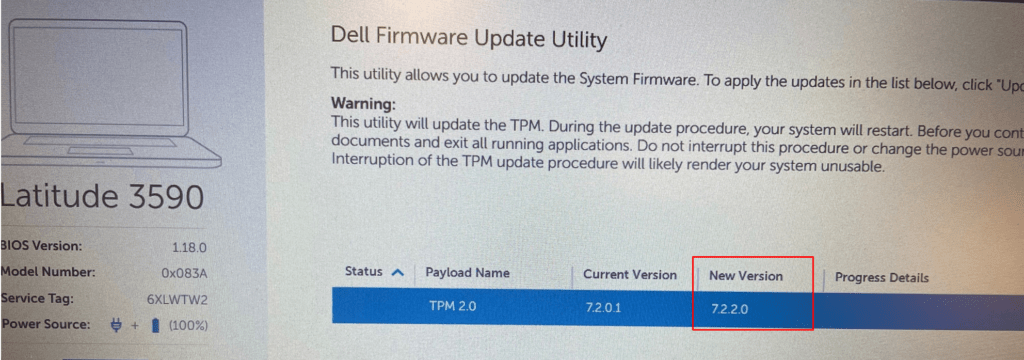
Because sometimes, even when the device tells you that it’s ready for attestation it doesn’t mean it’s ready for attestation. In one of my latest blogs, I showed you the fact that Microsoft also maintains a list of TPMs that have vulnerable firmware. Guess what Microsoft does with these naughty TPMs…. They will be blocked
Ready For Attestation False and the 0x81039001 TPM time-out (call4cloud.nl)
3. How to retry the Pre-Provisioning
If you end up with a Red Autopilot Screen mentioning that TPM attestation failed, you now know how to troubleshoot those attestation issues. If you have solved them, I assume you want to retry the Pre-Provisioning, right?
A possible solution is to reset the device, but if you don’t want to wait, just open this registry key
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Provisioning\AutopilotSettings
In this registry key, you need to delete 2 REG_SZ keys:
DevicePreparationCategory.Status
DeviceSetupCategory.Status
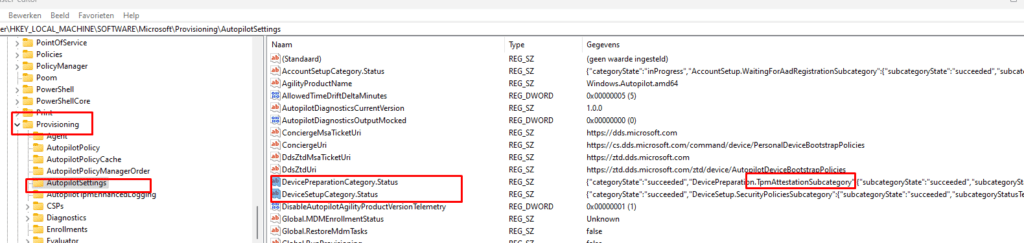
After you deleted those 2 registry keys, you need to run the “AikCertEnrollTask” as shown below
The device will restart the Aik Certificate Enrollment process in the background in a couple of seconds. If the scheduled task finishes without any errors, you can press the retry button again to retry the Autopilot pre-provisioning

If you want to read more about this wonderful “AikCertEnrolltask” scheduled task and TPM attestation, please read this blog below
Ready For Attestation False and the 0x81039001 TPM time-out (call4cloud.nl)
4. Test-AutopilotAttestation
You could always try out this PowerShell script when you don’t want to go through the hassle of trying to solve it manually. This PowerShell Script will try to test and remediate some attestation issues
PowerShell script to troubleshoot TPM attestation issues (call4cloud.nl)
Of course, it doesn’t solve “throttling” or “latency” issues at the service side at Microsoft. The latency issue is described in Microsoft in this incident: IT431147
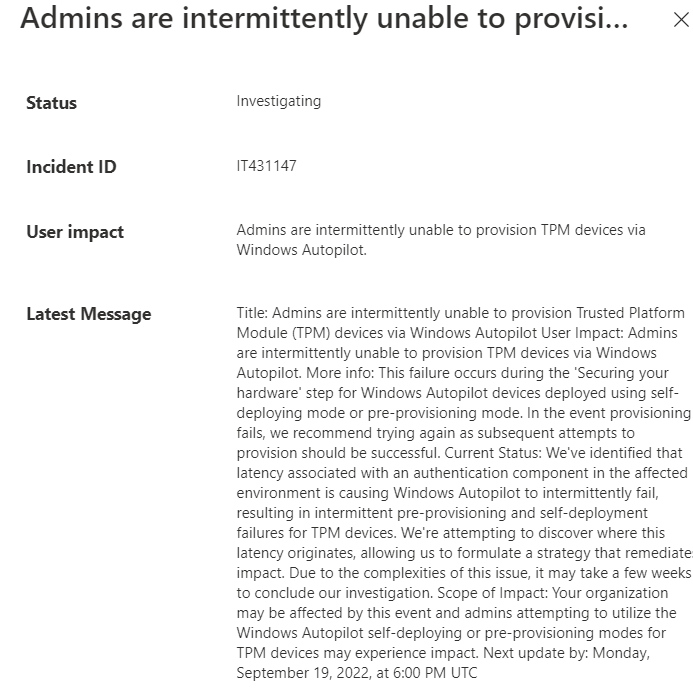
Conclusion:
Knowing how to troubleshoot can give you some insights into what’s happening or what could be wrong. I was expecting to see a Service warning in the Service Health and Message center…. but unfortunately, nothing was mentioned about this issue.
Sometimes it’s the Intel 11th gen issue, sometimes it’s just the TPM not supporting attestation, sometimes the EKCert can’t be retrieved, and sometimes Microsoft withdrew an AIK ca, and sometimes it’s just the need for patience…



When I run the certreq command, I have a STM-KeyID, not a NTC-keyID. Could that be the problem? This is an older Dell latitude 3400.
NTC or STM are just the shortnames of the tpm vendors..
STMicroelectronics and Nuvoton. so that shouldn’t be an issue
On a Dell Latitude 5421 with Windows 11 21H2.3 I get this same TPM attestation error when trying to provision, but provisioning works fine if I install Windows 10 on the same computer instead. Any idea?
Hi,
If that device has the Intel tiger lake tpm
Did you also made sure Windows 11 21h2 and that December build was installed? Because 21h2 did not fixed it, but the patch afterwards 🙂
thanks for information
And sometime, you just need a Firmware update to avoid this error.
Recently got this error on Lenovo M720q desktop computer (tpm firmware 7.63 updated to 7.85 to resolve the issue with tpm).
Yep… as also shown in this blog… https://call4cloud.nl/2020/12/the-red-screen-before-christmas/
Updating your firmware when you got attestation issues is and should always be step one
What to do when your key is listed in TrustedTpm.cab under “Removed the following AMD AIK Certificates”
Is there anything to do about that?
Does that mean it is blacklisted by microsoft and you will not be able to get the AK certificate I am missing?
It maybe also could be due to the service issues, but retrying does not help.
There are no updates available for the bios. It is a Lenovo AMD fTPM
{“Message”:”The authority \”amd-keyid-52fb59e29aa83a962fb9eef0fe5b4811de6b751e.microsoftaik.azure.net\” does not exist.”}
Most of the time when the key is removed from that document, it could be due to the tpm has vulnerable firmware… So .. 🙂 I guess you need to send out a support email to Lenovo and ask if there is a firmware update available for your device that could fix the vulnerability
Thank you, just ran though the guide and it helped with Error 0x81039023 on a Lenovo T16.
Had to go through it manually, the powershell script was giving me errors messages.
Hi Rudy,
I am running into the following errors 0x81039001 and 0x80190190 (both in your blogs).
When running the certreq command on the affected machines (affecting multiple machines of the same make/model) I get the following error: {“Message”:”No valid TPM EK/Platform certificate provided in the TPM identity request message.”}.
I have checked the TrustedTPM file from MS and my .cer appears on this list as recently as June, but am still getting the above error.
I have updated the TPM firmware to the latest available, reset TPM etc..
We have a ticket open with MS Support but no response at the moment.
Any ideas?
Thank you
My guess.. an infinion with the ca 035 aik url 🙂 ….
Thank you for your quick response.
Where do I go from here to fix in this case?
This has been happening for days and I’m losing patience! 🙁
Whilst diving into this error on an lenovo device I kept getting TPM attest errors, whilst above did not fix it I mightve found a fix for my use case (skipping it), which im sharing here, dumbfound but aslong as it works.. somehow the first step completed after this.
Clean install-> run this ps1 script and roll it in USER DRIVEN, autopilot (white glove) preprovisioning did not work on first attempt.
# Maak de benodigde mappen en sleutel aan
New-Item -Path “HKLM:\SOFTWARE\Microsoft\Mdm” -Force
New-Item -Path “HKLM:\SOFTWARE\Microsoft\Mdm\PolicyManager” -Force
New-Item -Path “HKLM:\SOFTWARE\Microsoft\Mdm\PolicyManager\AdmxDefault” -Force
New-Item -Path “HKLM:\SOFTWARE\Microsoft\Mdm\PolicyManager\AdmxDefault\SecureBoot” -Force
# Voeg de sleutel toe om TPM-attestatie te skippen
Set-ItemProperty -Path “HKLM:\SOFTWARE\Microsoft\Mdm\PolicyManager\AdmxDefault\SecureBoot” -Name AllowSkipTPMAttestation -Value 1
# Bevestig de gemaakte wijzigingen
Get-ItemProperty -Path “HKLM:\SOFTWARE\Microsoft\Mdm\PolicyManager\AdmxDefault\SecureBoot”
Write-Host “De registerwaarde is succesvol ingesteld!” -ForegroundColor Green
Hi thanks! where did you found this part: AdmxDefault\SecureBoot” -Name AllowSkipTPMAttestation -Value 1
But… user driven doesnt really needs tpm attestation to continue ..what error did you get if you just enroll it with user driven?
Hi Rudy, you’re quick!
Thanks for reformatting above text, I was in a hurry whilst wanting to share a possible workaround.
We’re migrating devices from Windows 10 to 11 whilst I stumbled upon this TPM attest error on this laptop.
Whilst Autopilot for pre-provisioning deployments is our standard, the rare case where user driven is needed I take it as a win after struggling for a full day just attempting to get it to work on either method.
In both cases I was getting error: 0x800705b4 as it failed the first step in every attempt.
The specific device was a lenovo thinkbook 15 g3 acl (model 21A4) and Intune reports it fully compliant now.
Thanks.
Mmm… so.. user enrollment autopilot also got you that time out error.. do you have a screenshot of that or some logs (as i have a feeling why it breaks….. the new enrollment mdm attestation that has been put in place…)